1. Preparation
Sophos UTM can connect with Microsoft Azure, site to site VPN in Static routing VPN Gateway.
The basic requirement is in below table:
The table below lists the requirements for both static and dynamic VPN gateways.
| Property | Static Routing VPN gateway | Dynamic Routing VPN gateway | High Performance VPN gateway |
| Site-to-Site connectivity (S2S) | Policy-based VPN configuration | Route-based VPN configuration | Route-based VPN configuration |
| Point-to-Site connectivity (P2S) | Not supported | Supported (Can coexist with site-to-site connectivity) | Supported (Can coexist with site-to-site connectivity) |
| Authentication method | Pre-shared key |
|
|
| Maximum Number of Site-to-Site (S2S) connections | 1 | 10 | 30 |
| Maximum Number of Point-to-Site (P2S) connections | Not supported | 128 | 128 |
| Active Routing Support (BGP) | Not supported | Not supported | Not supported |
Note that for the remainder of this page, the specifications for High Performance VPN gateway and Dynamic Routing VPN gateway are the same unless otherwise noted. For example, the validated VPN devices that are compatible with Azure Dynamic Routing VPN gateways will also be compatible with the new Azure High Performance VPN gateway.
Microsoft Document:
https://msdn.microsoft.com/en-us/library/azure/jj156075.aspx
https://msdn.microsoft.com/en-us/library/azure/dn133795.aspx
2. Configuration in Microsoft Azure
2.1. Log in to the Management Portal.
2.2. Network Services
In the lower left-hand corner of the screen, click New. In the navigation pane, click Network Services, and then click Virtual Network. Click Custom Create to begin the configuration wizard.
2.3. Virtual Network Details
On the Virtual Network Details page, enter the information below. For more information about the settings on the details page, see the Virtual Network Details page.
- Name – Name your virtual network. For example, EastUSVNet. You’ll use this virtual network name when you deploy your VMs and PaaS instances, so you may not want to make the name too complicated.
- Location – The location is directly related to the physical location (region) where you want your resources (VMs) to reside. For example, if you want the VMs that you deploy to this virtual network to be physically located in East US, select that location. You can’t change the region associated with your virtual network after you create it.
2.4. DNS Servers and VPN Connectivity
· DNS Server and IP: optional
· Check: Configure Site-To-Site VPN
2.5. Site-To-Site Connectivity
· Name: Name of local Network site
· VPN Device IP Address: Public IP Address of Sophos UTM
· Address Space: Subnet of Sophos UTM local network, which want to connect with Microsoft Azure. Multi subnet is allowed
2.6. Virtual Network Address Spaces
The subnet of Microsoft Azure Network:
· Address Space – including Starting IP and Address Count. Verify that the address spaces you specify don’t overlap any of the address spaces that you have on your on-premises network.
· Add subnet – including Starting IP and Address Count. Additional subnets are not required, but you may want to create a separate subnet for VMs that will have static DIPS. Or you might want to have your VMs in a subnet that is separate from your other role instances.
· Add gateway subnet – Click to add the gateway subnet. The gateway subnet is used only for the virtual network gateway and is required for this configuration.
2.7. Complete
Click the checkmark on the bottom of the page and your virtual network will begin to create. When it completes, you will see Created listed under Status on the Networks page in the Management Portal.
2.8. Go to Dashboard
· Create NEW Gateway
· Choose Static Gateway
2.9. Get the Gateway IP Address
· See the Microsoft Azure Gateway IP Address after create gateway successful.
2.10. Create the Preshare key
· Create the key, copy to paste to Sophos UTM configuration
3. Configuration the Sophos UTM
3.1. Add Remote Gateway
Go to Site-to-Site VPN -> IPSec -> Remote Gateway -> New Remote Gateway
3.2. Create New IPSec Policy
Note: IPSec PFS: None
3.3. Create new IPSec Connection:
· Remote gateway: Microsoft Azure
· Local Interface: WAN (which has the IP address in step above)
· Policy: Azure (create above)
· Local Network: 172.16.17.0/24 (create in step)
3.4. Enable Connection and Connect
See in Sophos UTM:
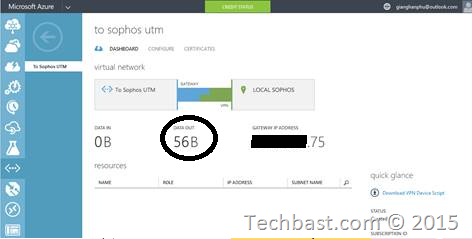
See in Microsoft Azure















Hello there, You have performed a great job. I’ll certainly digg it and for my part suggest to my friends. I’m sure they’ll be benefited from this website.
Nice article, got my UTM and Azure connected using these steps.
Thanks,
Tom
Thank you for such a great and detailed instruction! Any chance you could also add some more details on how to create another subnet in azure in the same address space and make it routable with on prem vlans?
This is Great. I made some modifications to my connection for the Policy based on your information. I hope that it stays up and running. the issue I have been having is that it keeps loosing connection with the VPN in azure. One minute it is able to ping and get through the next it is out. I restart VPN tunnel on the Sophos UTM and it comes right back up. I am not sure what is causing this I am hoping the changes I made to the Policy fix this issue.
Donovan,
Or others including the original poster, have you seen any improvement to frequent connection issues requiring you to reset the tunnel to fix it? We are also seeing this problem.
Thanks
Where can i generate the pre-shared key? tnx
I know this is an old topic, but I also had the disconnecting problem.
Looks like it’s because the IKE SA Lifetime needs to be 10800 instead of 7800.
See https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpn-devices for more info.
Other than that, great article that got my Azure VPN up and running 🙂
This won’t work if you need multiple site-to-site tunnels. Please read this guide instead.
https://github.com/mariodivece/strongswan-bridge-guide
Great work,. It was very easy to follow your step to step guide. Working quite well. thanks
I had this setup working properly for a whole year with Lifetime 28800 for the IKE but now all of a sudden I get disconnects when this key gets recreated after 28000 has anyone experience this here Azure links dropping at Re Key?