Some case you see the alert from Sophos UTM: Your Domain Controller is the Botnet.
The log:
2015:01:xx-xx:xx:10 SOPHOSUTM afcd[30448]: id=”2022″ severity=”warn” sys=”SecureNet” sub=”packetfilter” name=”Packet dropped (ATP)” srcip=”192.168.1.100″ dstip=”xxx.xxx.xxx.xxx” fwrule=”63001″ proto=”17″ threatname=”C2/Generic-A” status=”1″ host=”xyz.com” url=”-” action=”drop”
The alert email:
Advanced Threat Protection
A threat has been detected in your network
The source IP/host listed below was found to communicate with a potentially malicious site outside your company.
Details about the alert:
Threat name….: C2/Generic-A
Details……..: http://www.sophos.com/en-us/threat-center/threat-analyses/viruses-and-spyware/C2~Generic-A.aspx
Time………..: 2015-01-xx xx:xx:15
Traffic blocked: yes
Internal source IP address or host: Your Domain Controller IP
You need to check who’s query DNS to Domain Controller with the malicious domain by enable DNS logging:
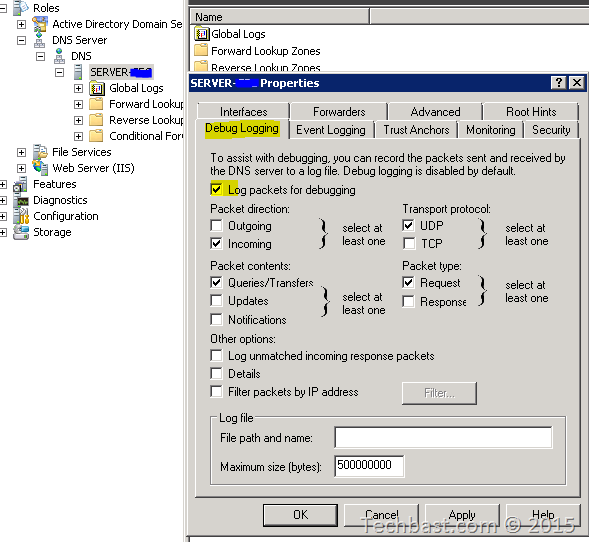
1. To get your Windows domain controller to log DNS lookups, follow the directions here:
- Open DNS.
- In the console tree, right-click the applicable DNS server, then click Properties.
- Click the Debug Logging tab.
- Select Log packets for debugging, and then select the events that you want the DNS server to record for debug logging.
- Screenshot:
Once you see data in C:\windows\system32\dns\dns.log you know that it’s working. The output like this:
The client query mail.com is: 172.16.16.10

Leave a Reply