Why you should choice the Enterprise mode to authentication your wifi user. In this short video tutorial I’ll show you that…
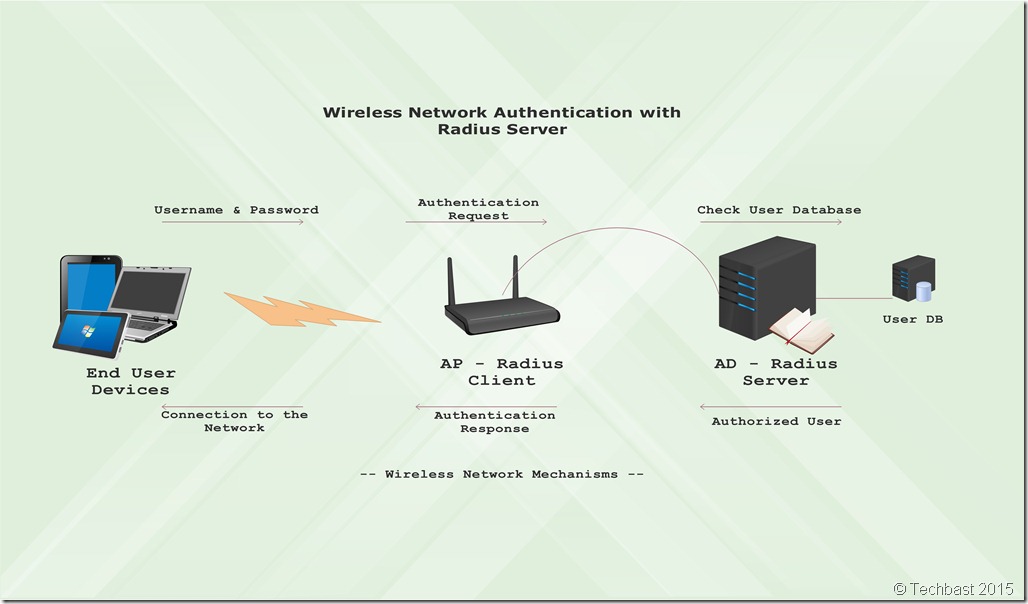
Network topology:
1. Benefits:
– End-users can logon with usernames and passwords.
– End-users securely receive unique encryption keys at each session.
– Administrator can change the login credentials and revoke access per user.
– This mode provides better encryption key security.
2. Contents:
– Setting up Access point as a Radius Client.
– Create test account and put them to allowed access Wifi group.
– Install Active Directory Certificate Services.
– Request Certificate.
– Install Network Policy and Access Service Role, DHCP Server.
– Configure Network Policy and Access Service Role.
– Configure Network Setting on Client Machines.
3. Prerequisite:
– 01 Windows Server 2012 R2 with AD promoted.
– 01 Windows 7 (Client Machine).
4. Assign IP address:
|
AD – Radius Server |
Access Point |
|
| IP Address |
192.168.1.10 |
192.168.1.252 |
| Subnet mask |
255.255.255.0 |
255.255.255.0 |
| Default gateway |
192.168.1.1 |
192.168.1.1 |
| Preferred DNS |
192.168.1.10 |
5. Implementation by Video:
Have fun!

This is really great stuff..Can you post a tutorial of complete configuration?
Great Article…Awesoime Video finally got Radius to work
Thank you. Many other useful articles waiting for you in Techbast, enjoy!
I am facing an issue while requesting a new certificate that i cannot see domain controller as an option. i only get the option of computer.
please let me know on how i can sort this out.
Thanks.
Hi Baptist,
Thank you for your interest in my articles.
May I know which server you are requesting certificate?
In my test-lab, I’m using AD + Radius on the same server.
If you do not use the same Radius and AD on the same server, you can ignore this step “Request certificate” make sure that on your radius server must be have “Active Directory Certificate Services” installed.
For Network Policy Server:
Network Policies => Open Your Policy => Constraints tab => Authentication Methods => on the right panel click “Microsoft: Protected EAP (PEAP)” => Edit => Certificate issued to: => choose your Certificate that you installed.
Great tutorial. I use RADIUS, AD, and DHCP all on separate servers. I also have a trusted CA from a provider (VeriSign). How can I make this work and will I also still need to install Certificate Services on the RADIUS? Please advise. Thank you.
also that i am trying to do, do you get the solution
Hello, does the server need to be a DC and CA for this? If we can get away from these, that’d be great as I as an admin don’t like promoting servers to DCs if they aren’t doing only DC stuff. Thank you.
Hi Eric,
You can run radius service without DC and CA, I think you may get a little more work than AD 🙂
If i use Smart phone access Wi-Fi, How i setup on my phone?
Hi Phan Trung,
Just put username/password on your Phone when connecting
I am trying to setup our Radius for the first time, any more articles in depth that show step by step? Thank you
I will post it asap, thank you for watching