
Overview
The SafeGuard Enterprise module File Encryption offers location-based file encryption on local drives and network locations, mainly for work groups on network shares.
In the SafeGuard Management Center, you define the rules for file-based encryption in File Encryption policies. In these File Encryption rules, you specify the folders that are to be handled by File Encryption, the encryption mode and the key to be used for encryption. In General Settings policies, you can define how specific applications and file systems are handled on endpoints in the context of File Encryption. You can specify ignored and trusted applications as well as ignored devices. You can also enable persistent encryption for File Encryption.
For encryption, Personal Keys can be used. A Personal Key that is active for a user only applies to this particular user and cannot be shared with or assigned to any other users. You can create Personal Keys in the SafeGuard Management Center under Users and Computers.
After a File Encryption policy has been assigned to endpoints, files in the locations covered by the policy are transparently encrypted without user interaction:
- New files in the relevant locations are encrypted automatically.
- If users have the key for an encrypted file, they can read and modify the content.
- If users do not have the key for an encrypted file, access is denied.
- If a user accesses an encrypted file on an endpoint where File Encryption is not installed, the encrypted content is shown
How to config
On Sophos SafeGuard Server
- Login to SafeGuard Management Center by Admin account
- Choose Policies -> Right click on Policy Items -> New -> File Encryption
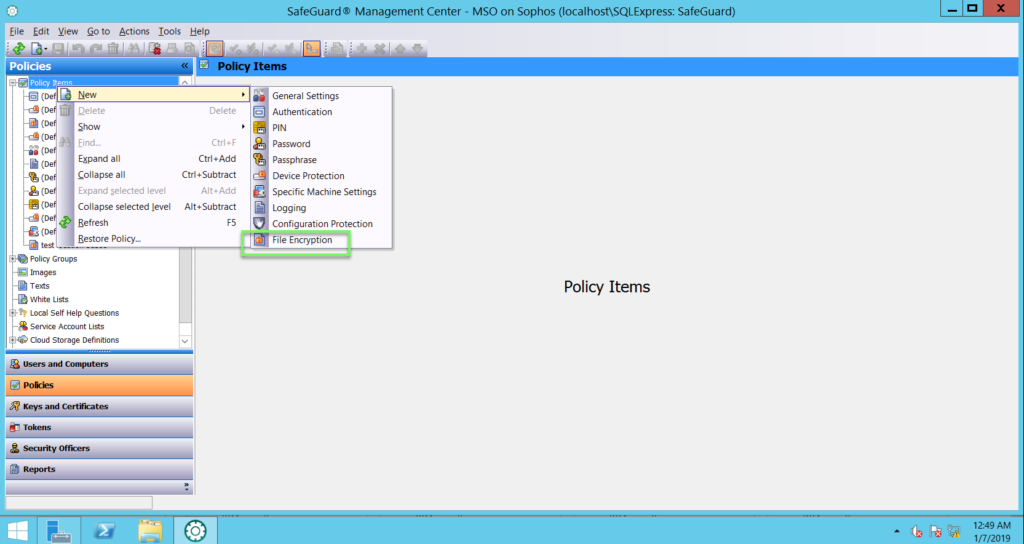
- Import Name -> click OK
- In Encryption type -> choose Location-based
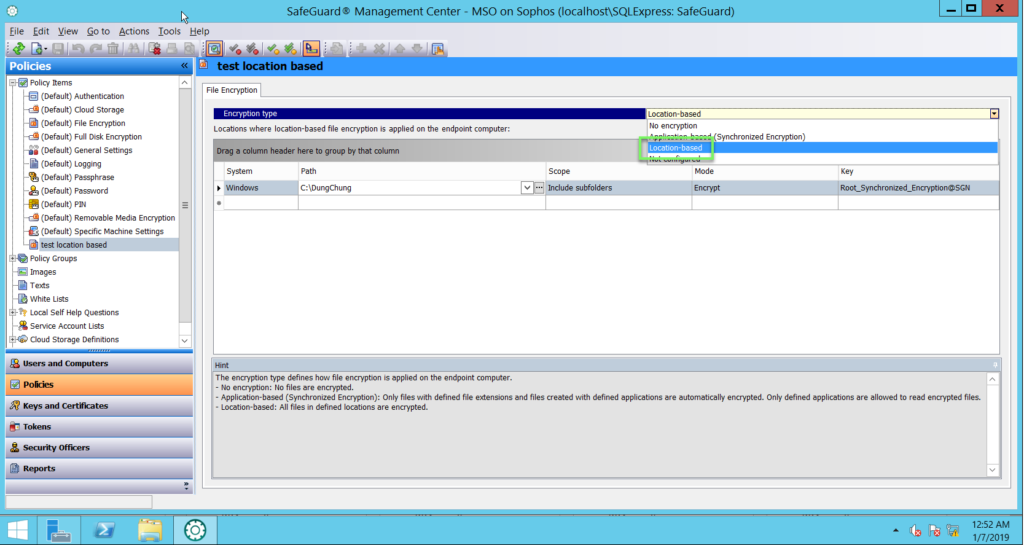
In the Path column -> set the path to be handled by File Encyption
- Click the drop-down button and select a folder name placeholder from the list of available placeholders
- Click the Browse button to browse the file system and select the required folder
- Alternatively, just enter a path name
In the Scope column, select one of the following
- Only this folder to apply the rule only to the folder indicated by the Path column
- Include subfolders to also apply the rule to all its subfolders
In the Mode column, define how File Encryption should handle the folder indicated in the Path column
- Select Encrypt to encrypt new files in the folder. The contents of the existing encrypted files are decrypted transparent when a user with the required key accesses them. If the user does not have required key, access is denied
- If you select Exclude, new files in the folder are not encrypted. You might use this option to exclude a subfolder from encryption if the parent folder is already covered by a rule with the Encrypt option
- If you select Ignore, files in the folder are not handled by File Encryption at all. New files are saved in plaintext. If a user accesses already encrypted files in this folder, the encrypted content is displayed, regardless whether the user has the required key or not
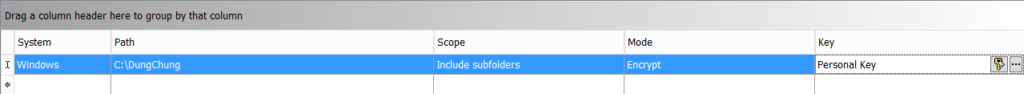
In the Key column, select the key to be used for the Encrypt mode. You can use keys created and applied in Users and Computers
- Click the Browse button to open the Find Keys dialog. Click Find now to display a list of all available keys and select the required key
- Click the Personal Key button with the key icon, to insert the Personal Key placeholder in the Key column. On the endpoint, this placeholder will be resolved to the active Personal Key of the logged on SafeGuard Enterprise user. If the relevant users do not have active Personal Keys yet, they are created automatically. You can create Personal Keys for single or multiple users in Users and Computers
-> Click Save
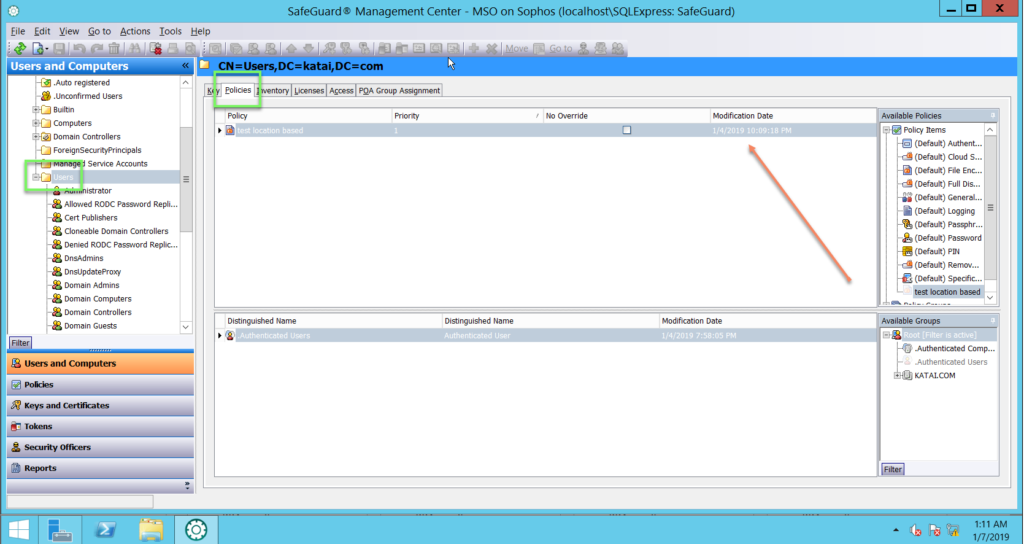
- In Users and Computers -> choose User -> click Policies -> drap and drop that policy -> click Save
Leave a Reply