
Purpose of the article
- This article describes steps to configure multiple IPsec VPN connections for redundancy. If the ISP1 Internet VPN link does not work, the ISP2 Internet VPN link will replace.
Network Diagram and scenario
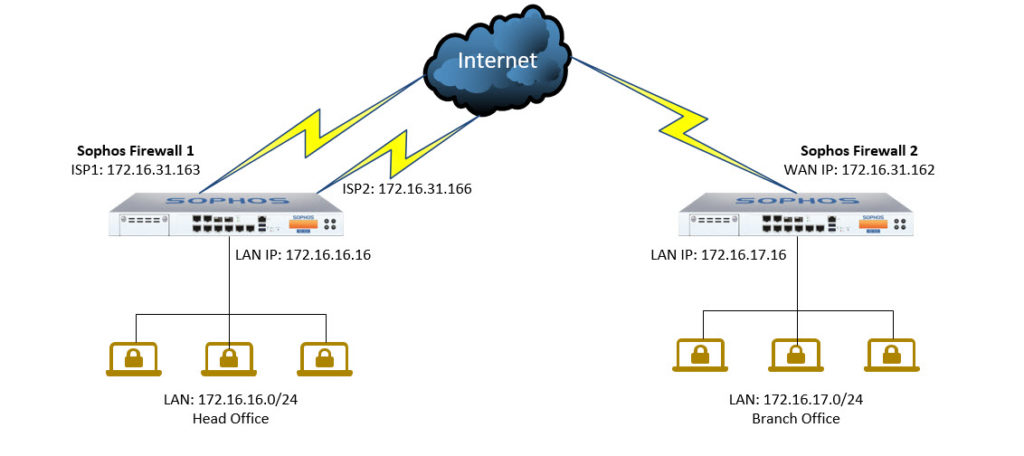
- In this diagram we have firewall device SF1 (Sophos Firewall 1) and SF2 (Sophos Firewall 2)
- SF1 has 2 WAN line : ISP1, ISP2 and SF has a WAN line.
- First, we will configure IPSec between two lines of SF1 and one WAN of SF2 and then configure Failover on SF2. When a VPN on SF1 is turned off, a failover VPN on ISP takes place. .
Configuring Sophos Firewall 1
Add local and remote LAN
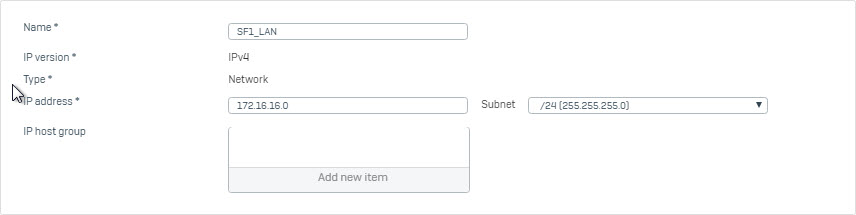
- Go to Hosts and Services > IP Host and click Add to create local LAN.
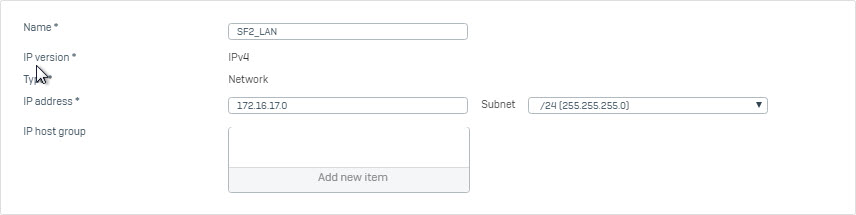
- Go to Hosts and Services > IP Host and click Add to create remote LAN.
Create an IPsec VPN connection
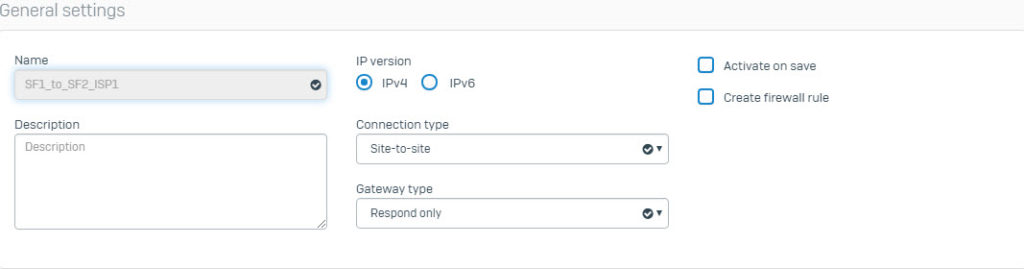
- Go to VPN > IPsec Connection and click Add. Create IPsec VPN connection using the following parameters and using IPS1 interface as the Listening Interface.
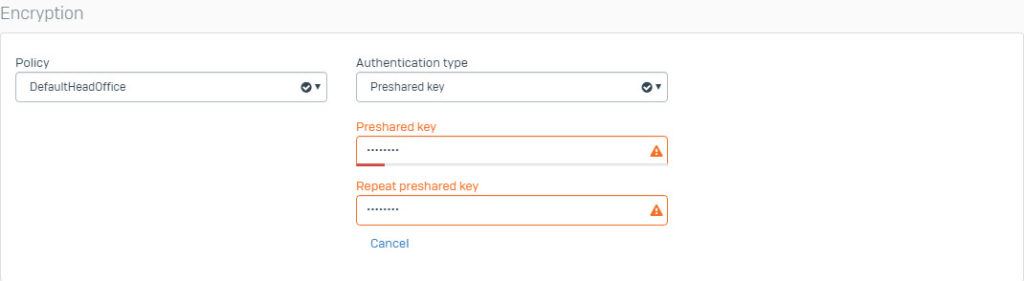
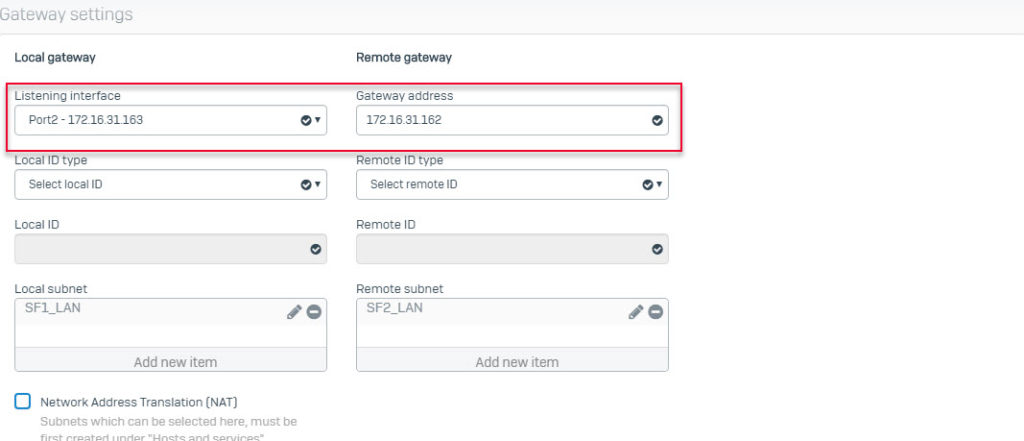

- Create another IPsec VPN connection using the following parameters and using ISP2 interface as the Listening Interface.
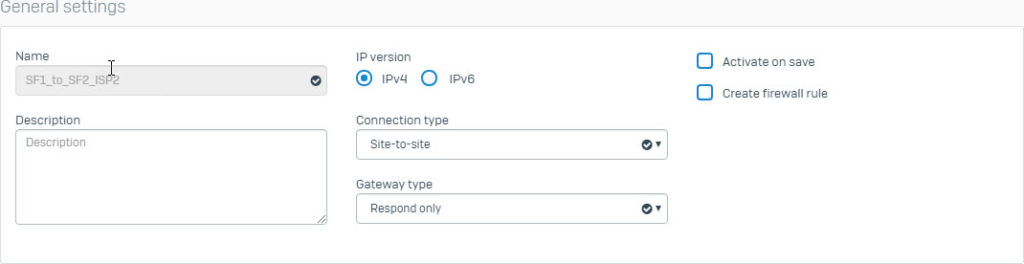
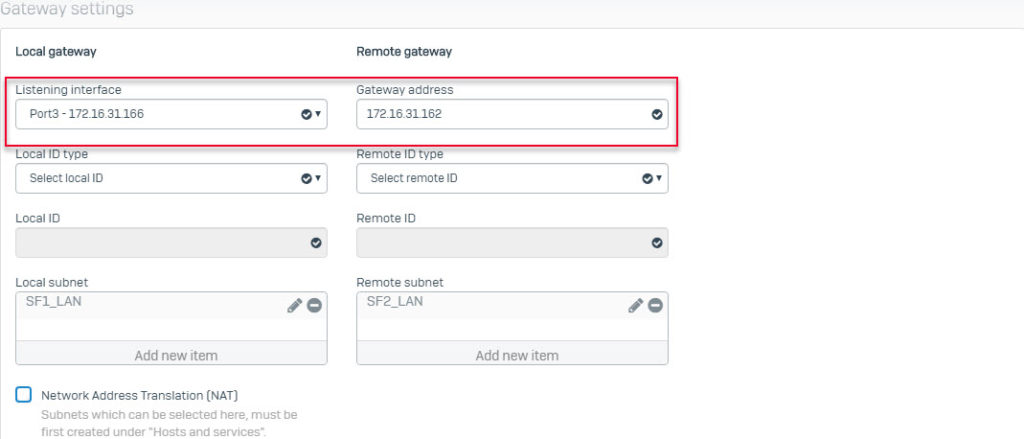
- The two IPsec VPN connections you just created will be displayed as follows.
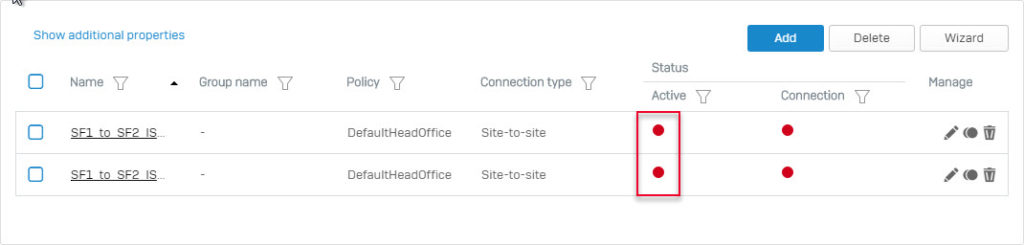
- Click on the red circle icon in the Status Active column to turn on these 2 VPN connections.
Add 2 firewall rule to allow traffic VPN
- Go to Firewall > +Add Firewall Rule. Create 2 User/Network Rule as shown below.
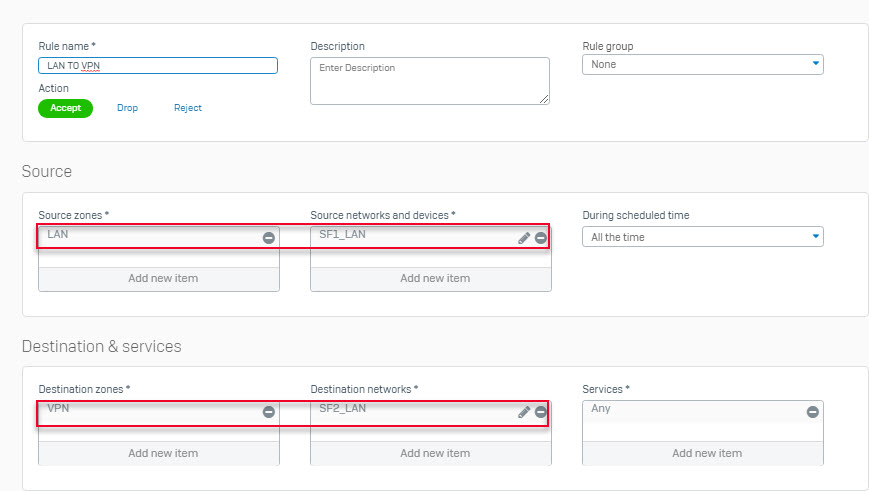
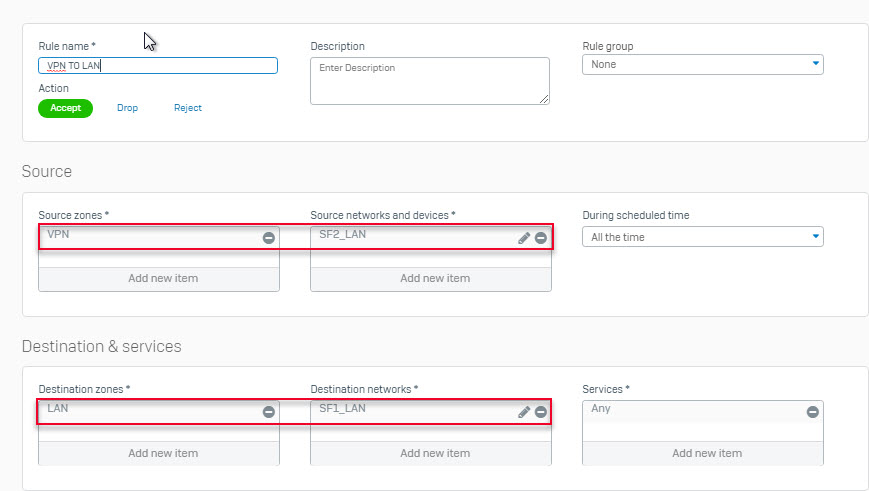
Configuring Sophos Firewall 2
Add local and remote LAN
- Go to Hosts and Services > IP Host and click Add to create local LAN.

- Go to Hosts and Services > IP Host and click Add to create remote LAN.

Create IPsec VPN connection
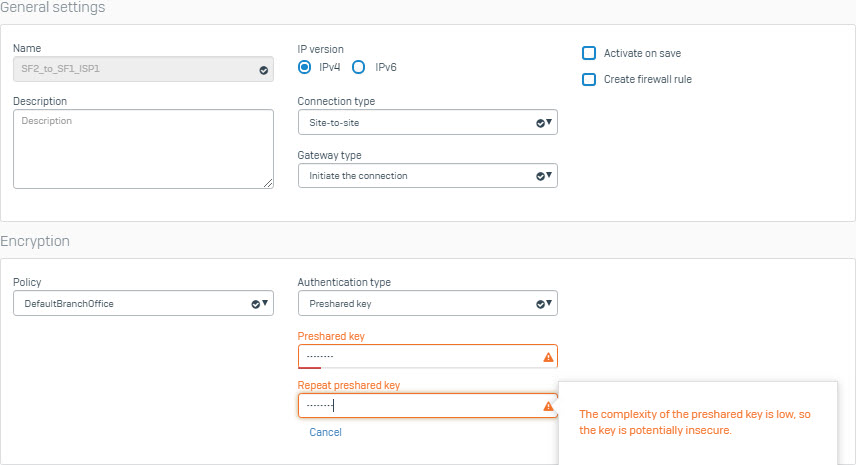
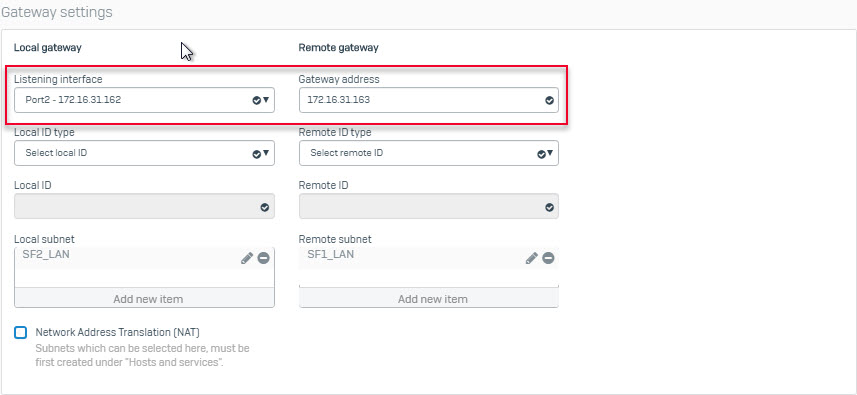
- Go to VPN > IPsec Connection and click Add. Create IPsec VPN connection using the following parameters and using IPS1 interface as theGateway Address.

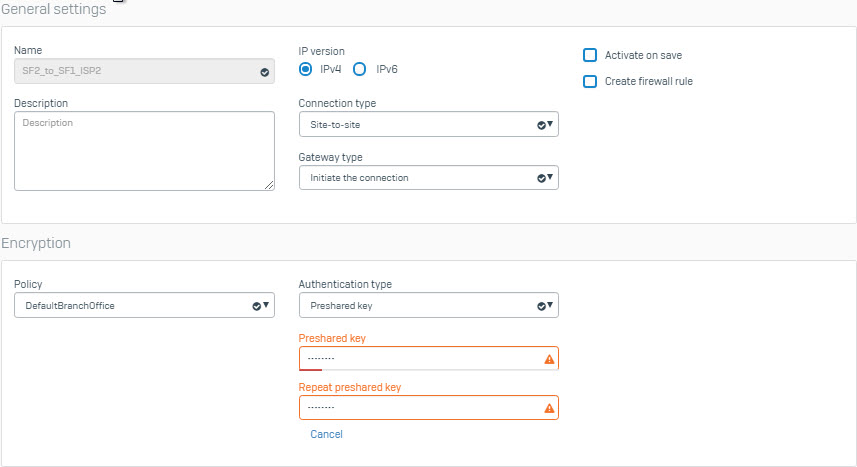
- Create another IPsec VPN connection using the following parameters and using ISP2 interface as the Gateway Address.
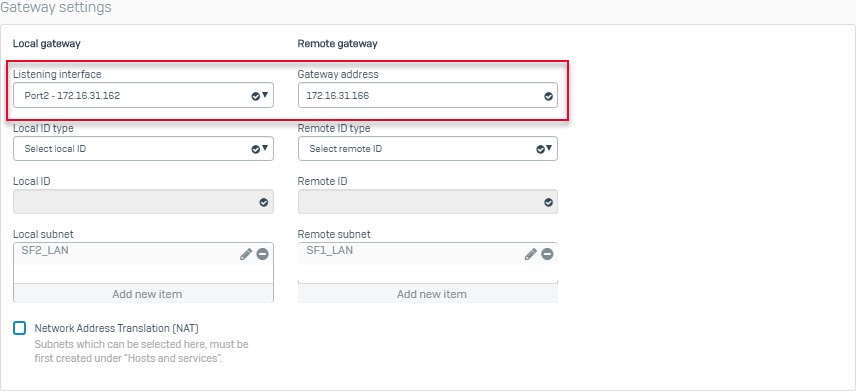

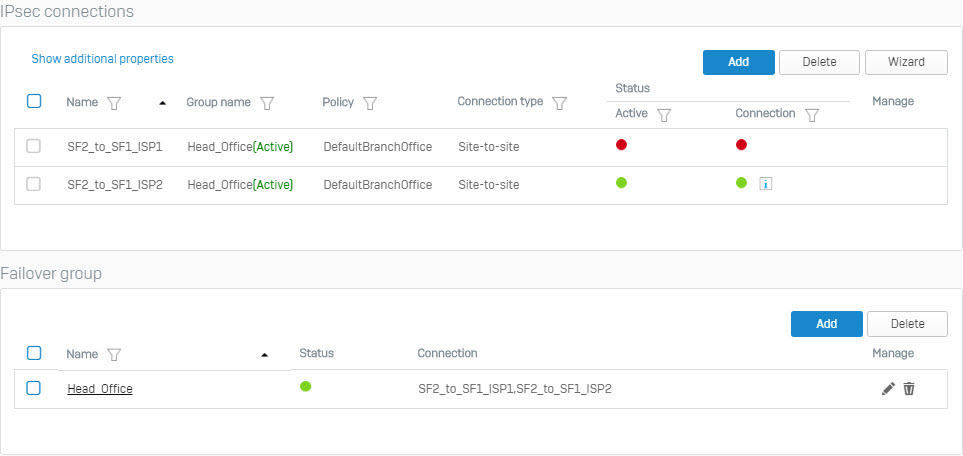
- The two IPsec VPN connection you just created will be displayed as follows.
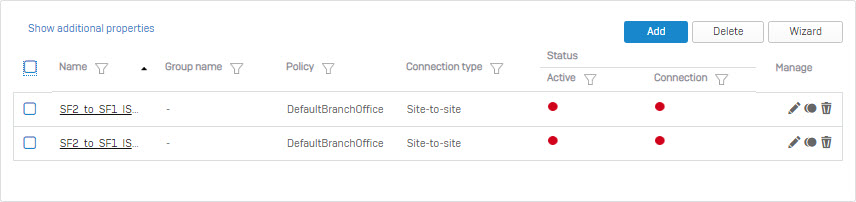
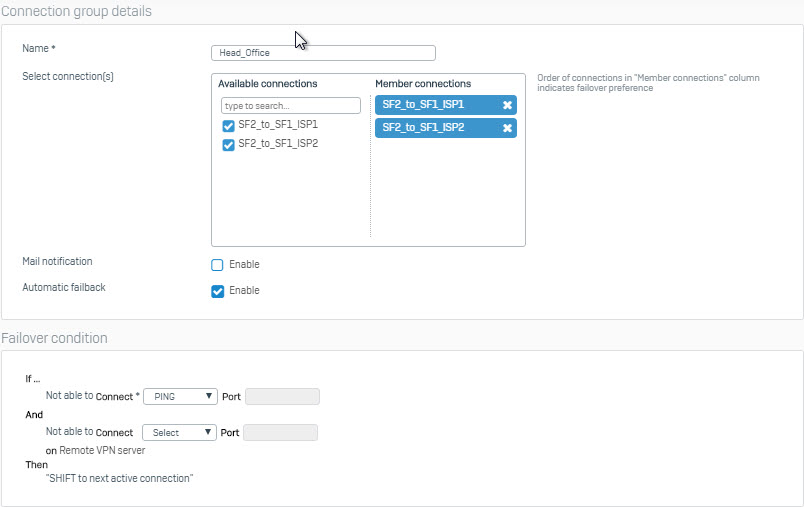
- Under Failover Group section click Add.
- Configure Failover according to the following parameters and click Save.
- Note: Starting with SFOS version 17.5, you can enable Automatic Failback to switch back to the primary IPsec VPN connection when it restored.
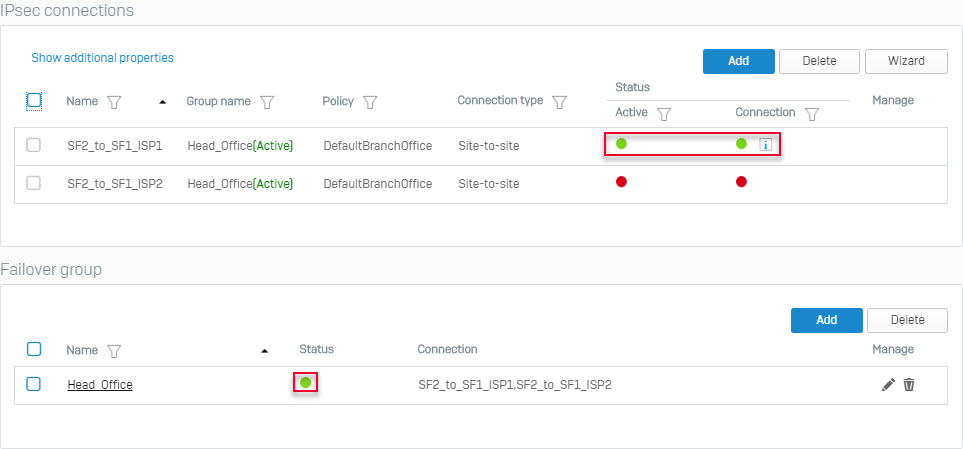
- The following screen will be displayed for the Failover Group section.
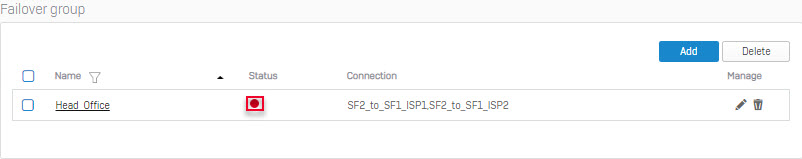
- Click the red circle icon under the Failover Group Status created to activate and set up the primary connection.
Add 2 firewall rule to allow VPN traffic


Result
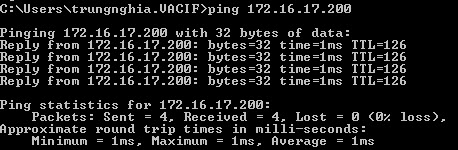
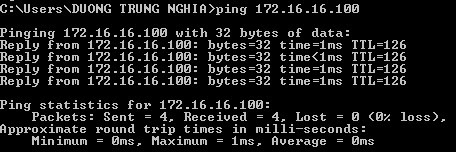
- A test ping from a machine behind Sophos Firewall 1 to a machine behind Sophos Firewall 2 and vice versa will work.
- Access the firewall rule list and verify that VPN rule firewalls allow incoming and outgoing traffic.

- Navigate Report > VPN and verify IPsec Usage.
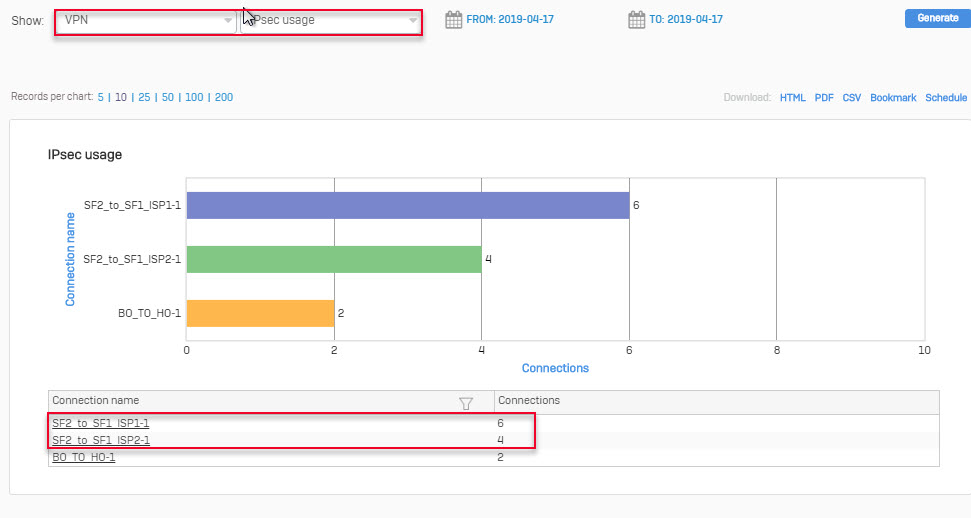
- Whenever the Internet ISP1 VPN link does not work, the IPsec connection will switch to the ISP2 Internet VPN link.
Note
- Make sure that VPN firewall rules are on the top of the firewall rule list.
- In a head and branch office configuration, the Sophos Firewall on the branch office usually acts as the tunnel initiator and the Sophos Firewall on the head office as a responder due to the following reasons:
- When the branch office device is configured with a dynamic IP address, the head office device cannot initiate the connection.
- As the branch offices number vary, it is recommended that each branch office retry the connection instead of the head office retrying all connections to the branch offices.
Good information. I have one query, Is it is required to add IPSEC_ROUTE in console for both the tunnels
It was not necessary, the policy did it instead