
1 Overview
Threat Hunting is an investigative tool which collects attack information on the organization’s endpoints. All events are collected through multiple sensors on the Harmony Endpoint and will be sent to Endpoint Service. You can check and Remediate the attack before it causes further damage.
Data will be saved in Service in 7 days, if you want more time to store data, you can buy the extended license for Harmony Endpoint.
2 User manual
Threat Hunting feature enabled by default.
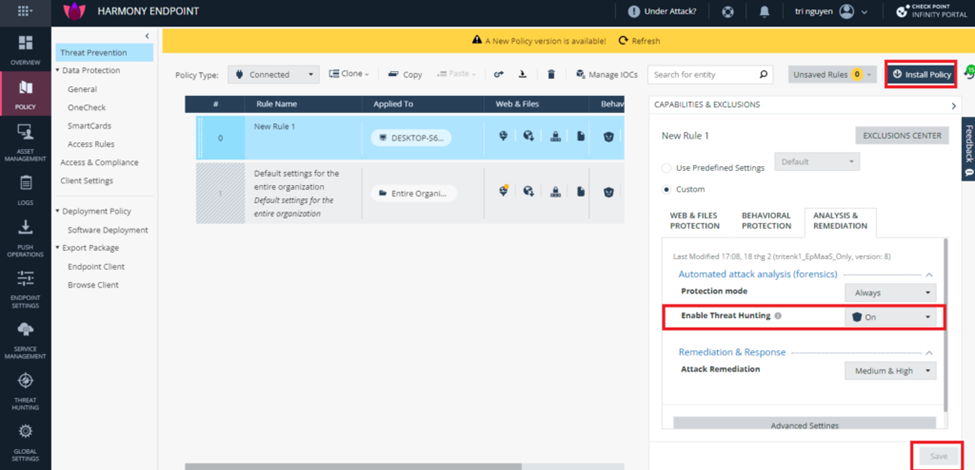
You can enter Policy > Threat Prevention > Analysis & Remediation. Then Enable Threat Hunting by selecting On and Click Save and Install Policy.
To use this, you enter Threat Hunting and this page will show up.
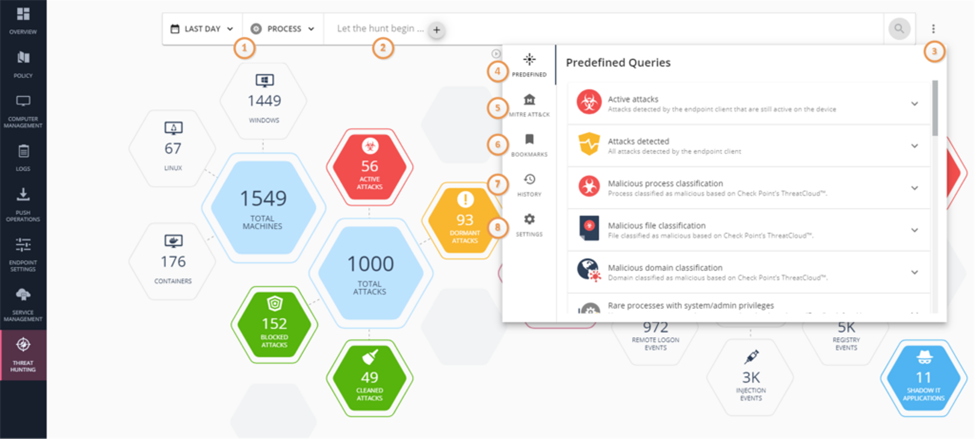
- 1 Filters your search results by date or process.
- 2 Here you can actively create search queries.
- 3 Menu for predefined queries.
- 4 Check Point’s predefined queries.
- 5 Mitre query
- 6 Here you can save all the queries that you ran.
- 7 Here you can see all the queries that you used.
- 8 Here you can changes the UI look and feel
2.1 Predefined Query
You can use Predefined Query, at the fourth item. Select queries you want to search and click run.
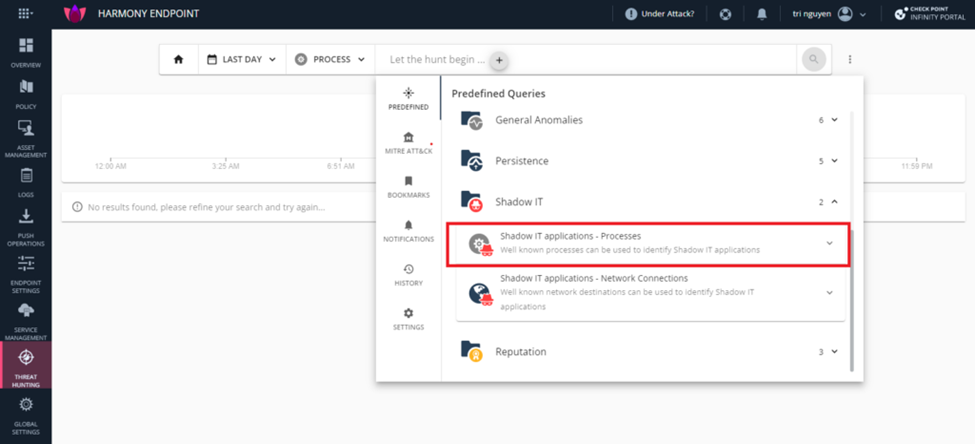
We will get the information by the query
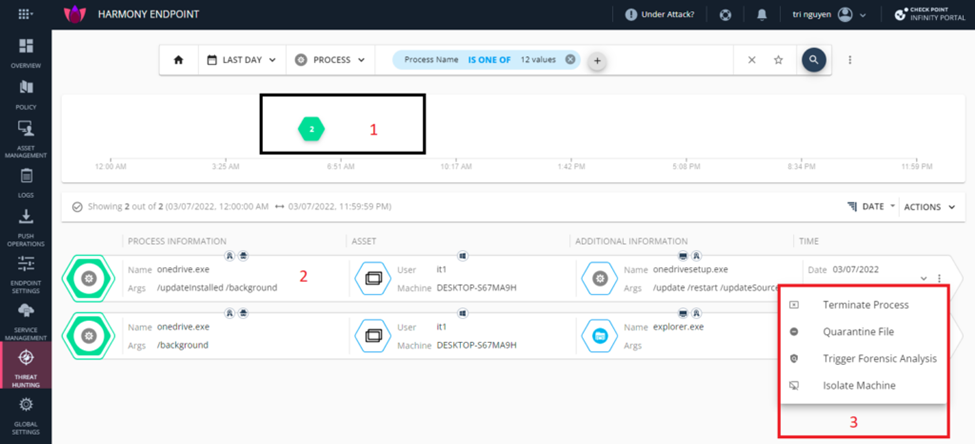
The first item is the timeline of this query, we click to show the detailed timeline.
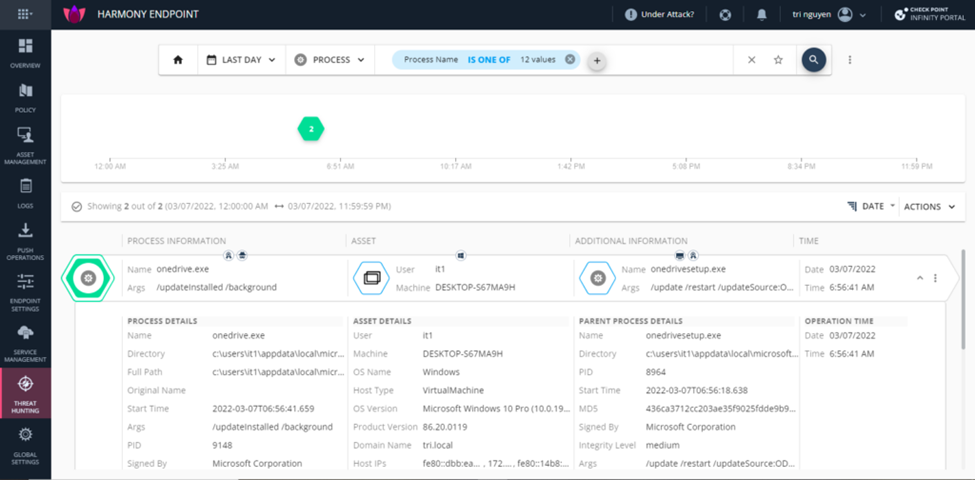
The second item is information from this query. You can see information by clicking on the down arrow at the end of this query.
At the third Item are the actions you can do with this query: Quarantine, Process termination, Full forensics analysis. Select at 3 dot at the end, this page will show up.
You select query and click down arrow to see information
2.2 Mitre ATT&CK
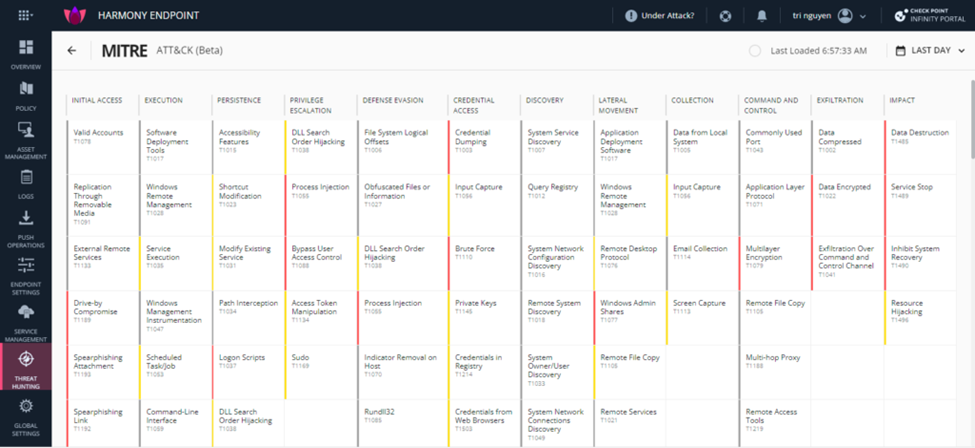
Mittre ATT&CK page will divide to 12 columns, one stand for 1 stage of the attack, consist of techniques. You click on one subject to see the query.
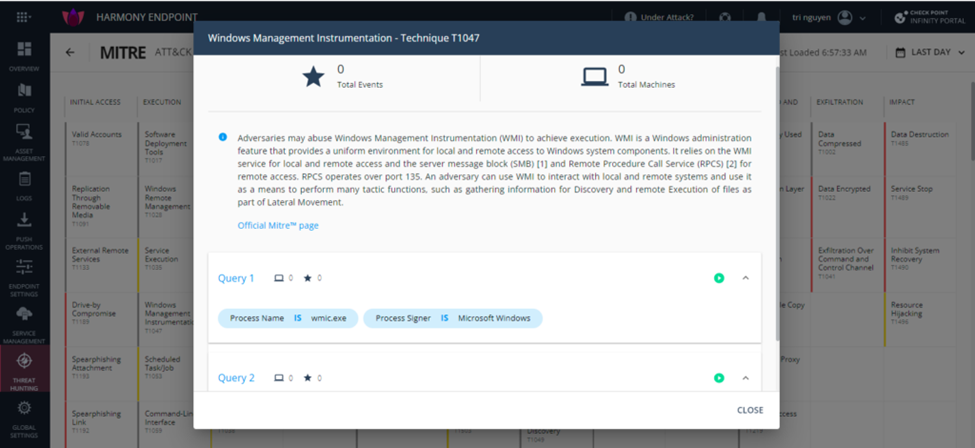
Example you want to search the security gap Windows Management Instrumentation T1047. You see in the Execution column and select the Windows Management Instrumentation section. Relevant Queries will show up, you can run a query to search for security gaps in your system.
2.3 Create Query
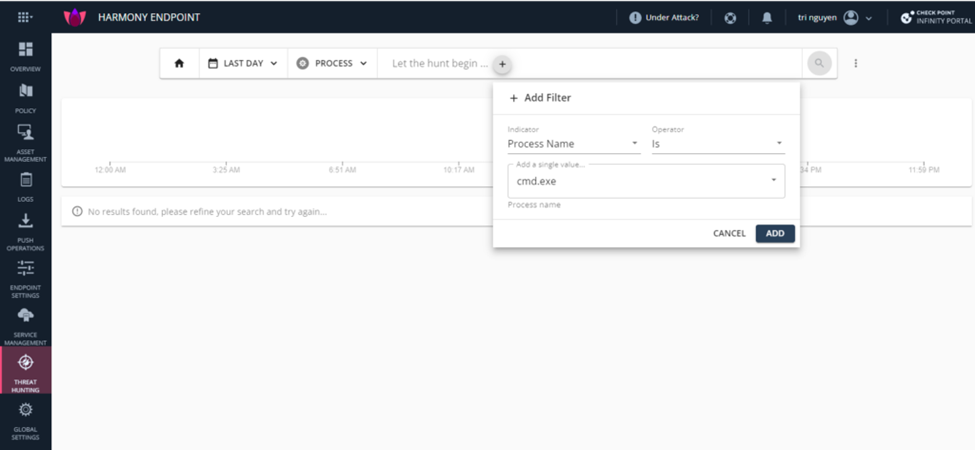
You can create your personal query. Select Let the hunt begin and click +. You can see options in this page where you can modify your query. Example, I want to search for a process whose name is cmd.exe.
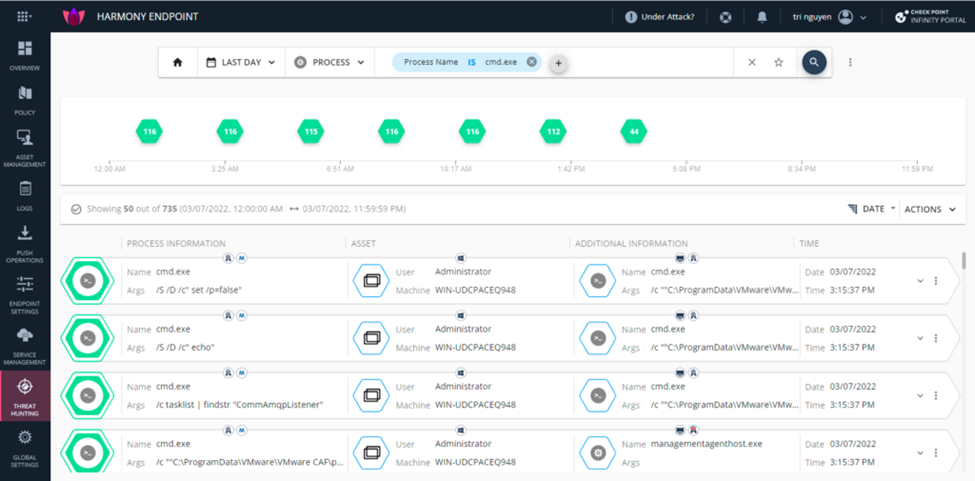
So we have finished understanding the Threat Hunting feature. Best regards.
Leave a Reply