STEP 1: CONFIGURING UTM
- Defining a user account
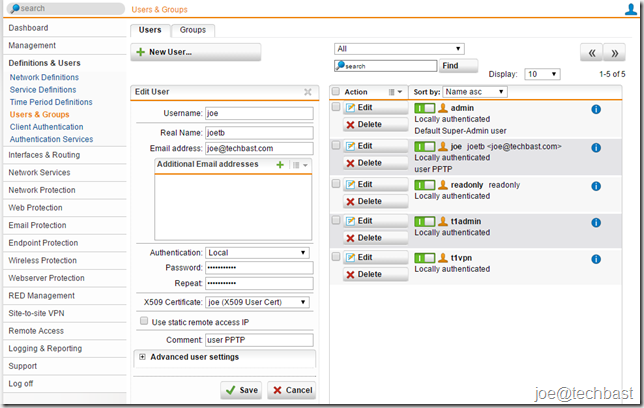
- Open Definitions & Users > Users & Groups > Users
- Click “New User” button
- Make the following setting:
- Username, Real name, Email address
- Authentication: Remote Access PPTP the “local” and “RADIUS” authentication methods are supported. With “local” authentication method, you will enter two fields password and repeat
- Click “Save”
- Configuring L2TPOver IPsec settings
- Open Remote Access > L2TP Over IPsec > Global tab
- Enable L2TP
- Make the following settings:
- Interface: Select the network interface to use for L2TP access.
- Authentication mode: Select the authentication mode (Preshared key or X.509 CA Check)
- Preshared key: enter the shared secret. This is secure phrase or password that is used to set up the secure tunnel.
- X.509 CA Check:
Certificate: Select the local X.509 certificate to authenticate the server.
- Assign IP addresses by: Select IP address pool or DHCP Server
- IP address pool: default IP address 10.242.1.x/24, Network is called VPN Pool (PPTP). D
- DHCP server (DHCP server Via interface)
- Authentication via: Select authentication method “local” or “RADIUS”
- Users and groups: When you using local authentication, please select the users or groups that should be able to use PPTP remote access.
- Click Apply to save your settings
- Configuring Advanced L2TP over IPsec settings
- Open Remote Access > L2TP over IPsec > Debug tab
- IKE Debugging
- Control Flow: Displays control messages of IKE state
- Outbound Packets: Displays content of outgoing IKE messages
- Inbound Packets: Displays content of incoming IKE messages
- Kernel Messaging: Displays communication messages with the Kernel
- High Availability: Displays communication with other HA nodes
- Click Apply to save your settings
- Optionally, enable debug mode => click Apply
- Defining Firewall Rules
- Open Network Protection > Firewall > Rules tab
- Click “New Rule button “
- Make the following settings:
- Sources: Add the remote host or user
- Services: Add the allowed services
- Destinations: Add the allowed networks
- Action: Select Allow
- Click Save
- Enable the rule: clicking the status icon => status icon turns green
- Defining Masquerading Rules
- Open Network Protection > NAT > Masquerading tab
- Click New Masquerading Rule button
- Make the following settings:
- Network: Select network of the remote endpoint.
- Interface: Select interface.
- Use address: If the interface you selected has more than one IP address assigned, you can define here which IP address is to be used for masquerading
- Click Save
- Enable rule
- Optionally, activate the proxies
STEP 2: CONFIGURING REMOTE CLIENT
- Start your browser and open the User Portal => Log in to the User Portal => go to Remotes Access lab => view information L2TP Over IPsec (can review “preshred key”).

- Configuring Windows Client
- Click Start => Control Panel
- In the Control Panel, click Network and Internet => Network and Sharing Center => Set up a new connection or network
- Define the dial-up Internet connection
- Click Next
- Enter the hostname or the IP address of the gateway => Allow other people to use this connection
- Click Next
- Click Create
- Right-click the new connection and select Properties => Security => make information same picture follow:
- click OK
- Open Network => enter username and password => Connected
Done, Thanks you!












Thanks for the article but how do you configure the client if you are using the “X.509 CA Check” option?