- Login to Sophos SafeGuard by Admin account
- Choose Policies -> Policy Items -> (Default) Authentication
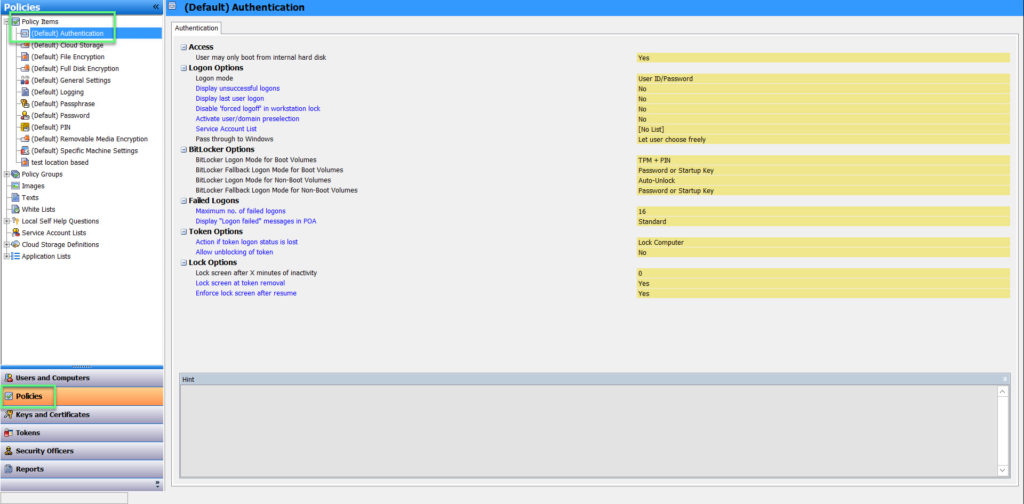
ACCESS
- Users may only boot from internal hard disk: Determines whether users may start the computer from the hard drive and/or another medium. Yes: Users can only boot from the hard disk. The SafeGuard POA does not offer the option to start the computer with a floppy disk or other external media. No: Users may start the computer from the hard disk, floppy disk or external medium (USB, CD etc.)
LOGON OPTIONS
- Logon mode:
- User ID/Password: Users have to log on with their username and password
- Token: The user can only log on to the SafeGuard POA using a token or smartcard. This process offers a higher level of security. The user is requested to insert the token at logon. User identity is verified by token ownership and PIN presentation. After the user has entered the correct PIN, Sophos SafeGuard automatically reads the data for user logon
- Fingerprint: Select this setting to enable logon with Lenovo Fingerprint Reader. Users to whom this policy applies can then log on with a fingerprint or a user name and password. This procedure provides the maximum level of security. When logging on, users swipe their fingers over the fingerprint, the SafeGuard Power-on Authentication process reads the user’s credentials and logs the user on to Power-on Authentication. The system then tranfers the credentials to Windows, and the user is logged on to the computer
- Logon options using token
- Non-crytographic: Authentication at SafeGuard POA and Windows based on user credentials. In Sophos SafeGuard only non-crytographic tokens can be used
- PIN used for autologon with token: Specify a default PIN to enable the user to automatically log on at the SafeGuard Power-on Authentication using a token or smartcard. The user is requested to insert the token at logon and is then passed through the SafeGuard Power-on Authentication. Windowns will be started. PIN rules do not need to be observed
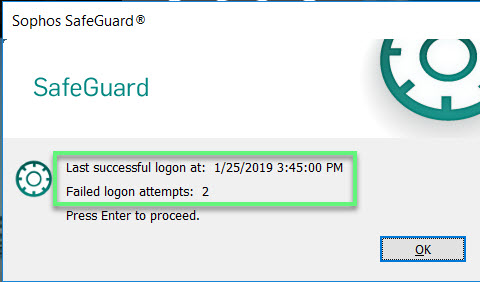
- Display unsuccessful logons for this user: Displays (settings: Yes) after logon at the SafeGuard POA and Windows a dialog showing information on the last failed logon (user name/date/time)
- Display last user logon: Display (setting: Yes) after logon at the SafeGuard POA and Windows a dialog showing information on the
- last successful logon (username /date/time)
- last user credentials of the logged on user
- Disable ‘forced logoff’ in workstation lock: If users wish to exit the endpoint for a short time only, they can click Block workstation to block the computer for other users and unlock it with the user password
- No: The user who has locked the computer as well as an administrator can unlock it. If an administrator unlocks the computer, the currently logged on user is logged off automatically
- Yes: Changes this behavior. In this case, only the user can unlock the computer. The administrator cannot unlock it and the user will not be logged off automatically
- Acticate user/domain preselection:
- Yes: The SafeGuard POA saves the user name and domain of the last logged on user. Users therefore do not need to enter their user names every time they log on
- No: The SafeGuard POA does not save the user name and the domain of the last logged on user
- Service Account List: To prevent administrative operations on a Sophos SafeGuard protected endpoint leading to an activation of the Power-on Service Account List Authentication and the addition of rollout operators as users to the computer, Sophos SafeGuard offers service account lists for Sophos SafeGuard endpoint. The users included in these lists are treated as Sophos SafeGuard guest users. Before you select a list here you must first create the lists in the Policies navigation area under Service Account Lists
- Pass through to Windows:
- Let user choose freely: The user can decide by selecting/deselecting this option in the SafeGuard POA logon dialog whether automatic logon at Windows is to be performed
- Enforce pass-through to Windows: The user will always be automatically logged on to Windows
- Disable pass-through to Windows: After the SafeGuard POA logon, the Windows logon dialog will be displayed.The user has to log on to Windows manually
BITLOCKER OPTIONS
- BitLocker Logon mode:
- TPM: The key for logon is stored on the TPM chip
- TPM + PIN: The key for logon is stored on the TPM chip and a PIN is also required for logon. Settings for the PIN are given under PIN and password
- USB Memory Stick: The key for logon is stored on a USB stick
- TPM + USB Memory Stick: The key for logon is stored on the TPM chip and on a USB stick. Logon can either be with the TPM chip or USB stick
- BitLocker Fallback Logon mode: In case logon fails, Sophos SafeGuard offers logon with USB stick as a fallback mechanism or an error message output
FAILED LOGONS
- Maximum no. of failed logons: Determines how many times a user can attempt to log on using an invalid user name or password. After incorrectly entering a Maximum no. of failed logons user name or password three times in a row for instance, a fourth attempt will lock the computer
- Display “Logon failed” messages in POA: Defines level of detail for messages on failed logons:
- Standard: Shows a short description
- Verbose: Displays more detailed information
TOKEN OPTIONS
- Action if token logon status is lost: Defines behavior after removing the token from the computer: Possible actions include:
- Lock Computer
- Present PIN dialog
- No Action
- Allow unblocking of token: Determines whether the token may be unblocked at logon
LOCK OPTIONS
- Lock screen after X minutes inactivity: Determines the time after which an unused desktop is automatically locked.The default value is 0 minutes in which case the desktop will not be locked
- Lock screen at token removal: Determines whether the screen is locked if a token is removed during a session
- Lock screen after resume: Determines whether the screen is locked if the computer is reactivated from standby mode
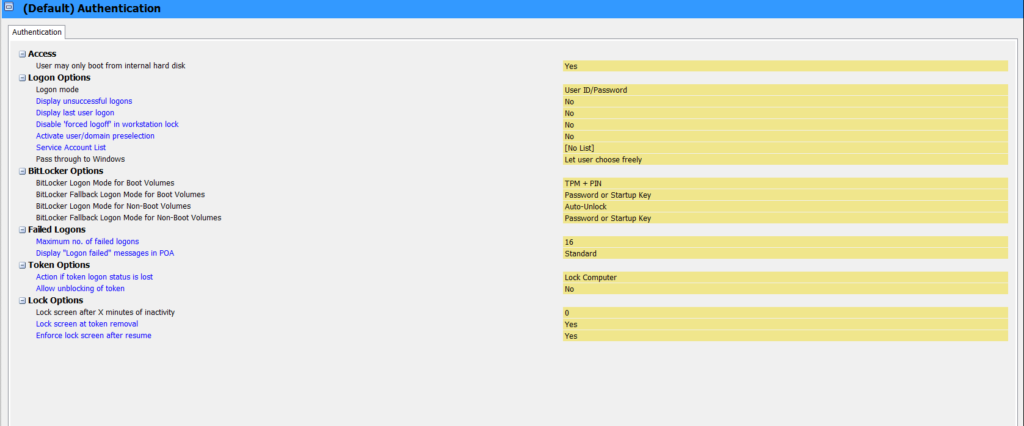
-> After config Authentication policy -> click Save
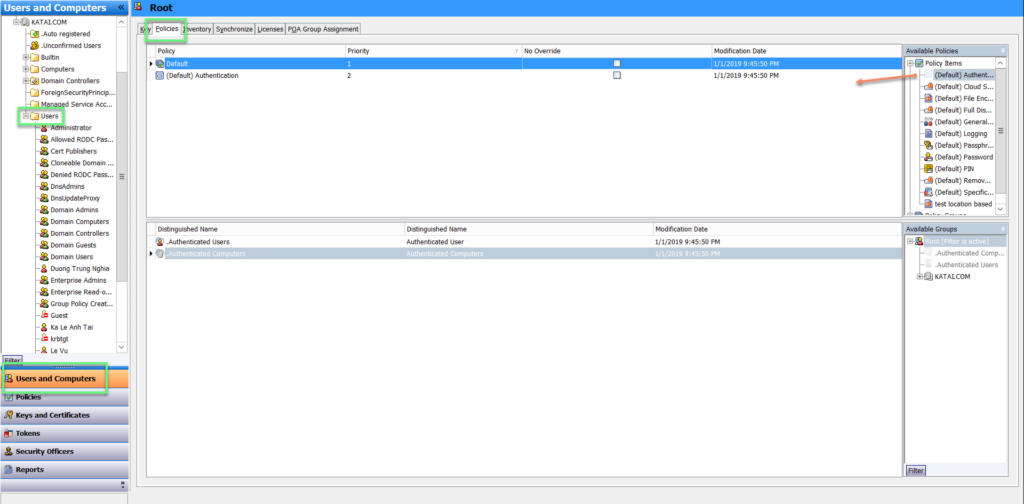
- Choose Users and Computers -> click Users -> Policies -> Drag and drop Policy in the right to main pane -> Click Save
- A notification will show when you logon to computer
Leave a Reply