
Introducing Phish Threat and Phish Threat emulation with Sophos Central Part 3
The goal of the article Following the article in Part 2, Part 3 will proceed with Phish Threat configuration with the third Campaings type Attachment Read More

The goal of the article Following the article in Part 2, Part 3 will proceed with Phish Threat configuration with the third Campaings type Attachment Read More

The goal of the article Following the article in Part 1, Part 2 will proceed with Phish Threat configuration with the second Campaings type Credential Read More

The goal of the article In part 1 of this article, what is Phish Threat? How to prevent Phish Threat attacks and introduce the Phish Read More
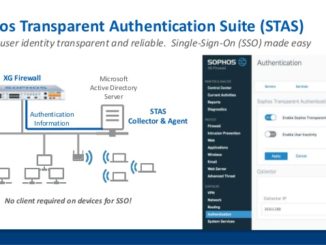
Overview Sophos Transparent Authentication Suite eliminates the need to remember multiple passwords when users log into Sophos UTM when he log in to Windows with Read More
Overview Captive Portal is a flexible feature, only available on large commercial firewall, this feature helps redirect the user’s browser to a predetermined website, thereby Read More

Overview This article introduces redundant power equipment for Sophos firewall devices (XG/SG External Redundant Power Supply) Supported devices for firewall device models below: Sophos SG Read More
Gradcrab 5.2 is the type of ransomware variant that encodes data that is spread by Phishing. An email with an attachment containing malicious code will Read More

This article will show you how to decrypt the drive after the drive has been encrypted using Sophos Central on Windows 10 and Windows 7. Read More

This article will describe the step configure Full Disk Encryption on Windows 7 using Sophos Central Diagram and Implementation steps As the diagram we see Read More

This article guides the steps to login when the user forgets the password on Windows 7 using Recovery Key Diagram and implementation steps As the Read More
Copyright © 2025 | WordPress Theme by MH Themes