Overview:
- This article describes the steps to configure a Site-to-Site IPsec VPN connection using preshared key as an authentication method for VPN peers.
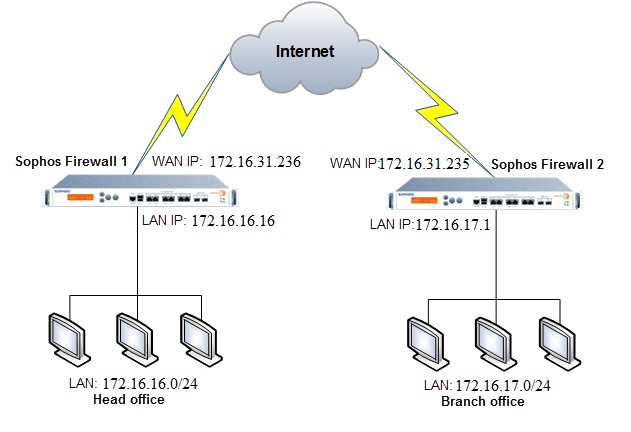
- We have the following diagram:
Configuring Sophos Firewall 1
Add local and remote LAN
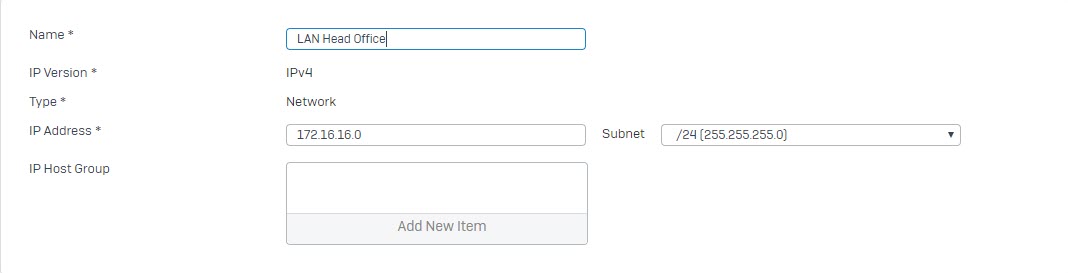
- Go to Hosts and Services -> IP Host and select Add to create the local LAN.
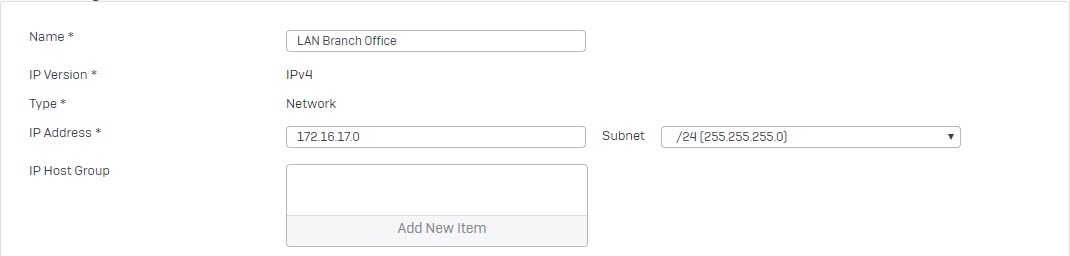
- Go to Hosts and Services -> IP Host and select Add to create the remote LAN.
Create an IPsec VPN Connection:
- Go to VPN > IPsec Connections and select Wizard. Give it a name and click on Start to follow the wizard.
- Select Site To Site as a connection type and select Head Office.
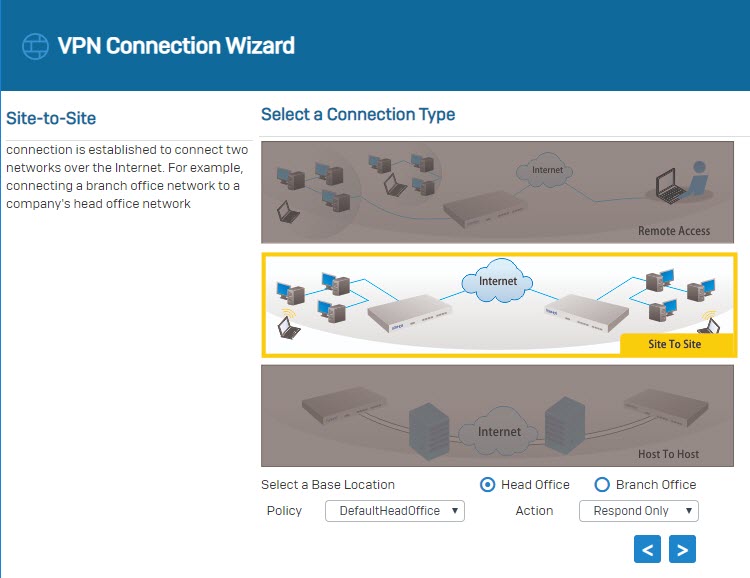
- Set the Authentication Type yp Preshared key.
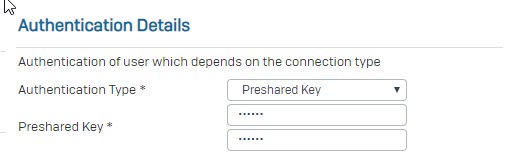
- In Local Subnet field, choose the local LAN created earlier.
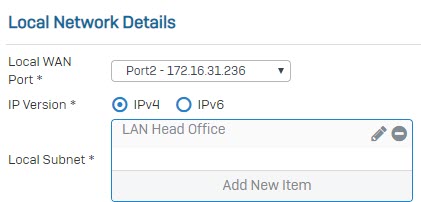
- In Remote VPN Server, enter IP WAN of Branch Office. In Remote Subnet field, choose the remote LAN create earlier.
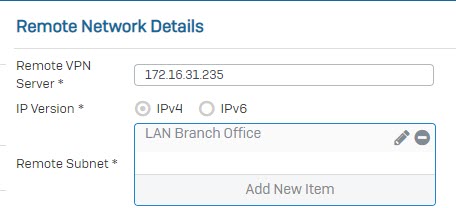
- In User Authentication Mode field, choose Disabled.
- Click Next again and click Finish.
- Click the
 under Status (Active) to activate the connection.
under Status (Active) to activate the connection.
![]()
![]()
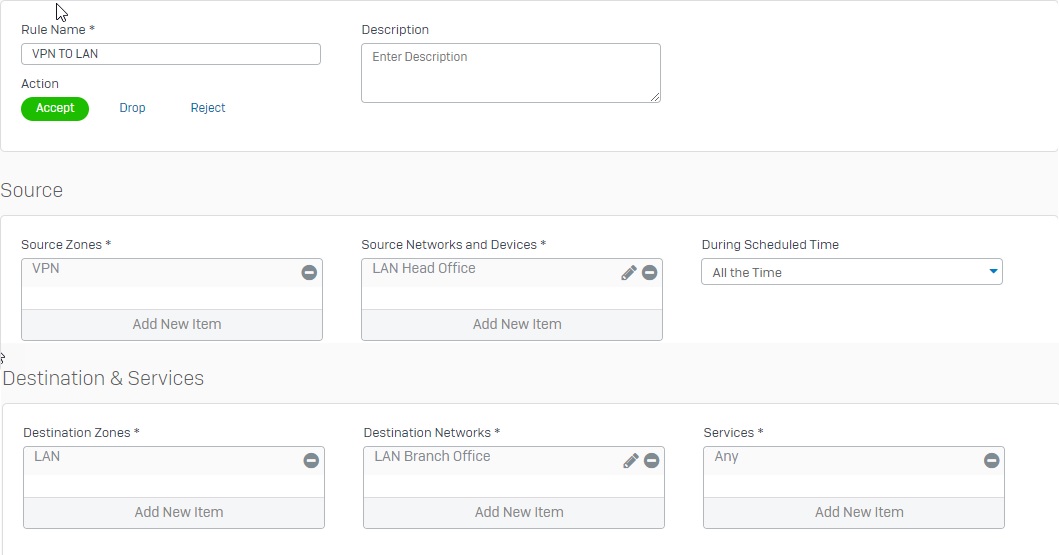
Add two firewall rules allowing VPN traffic
- Go to Firewall and click +Add Firewall Rule. Create two user/network rules as shown below.
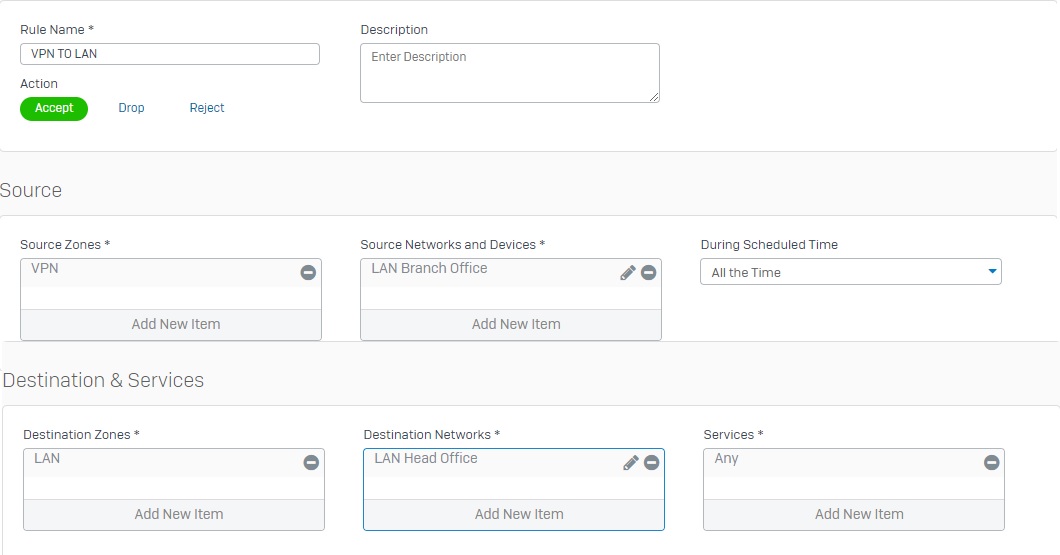
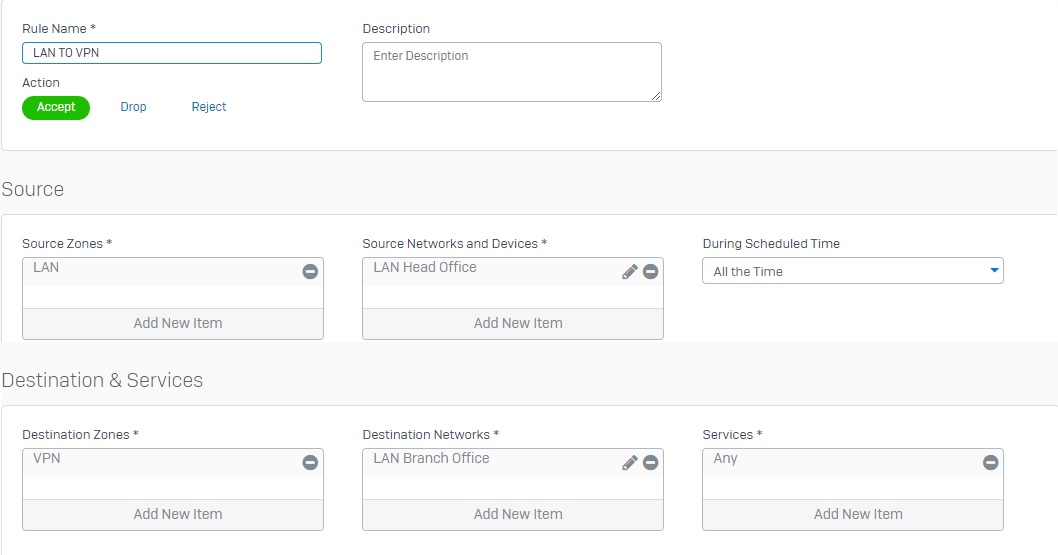
Configuring Sophos Firewall 2
Add local and remote LAN.
- Go to Hosts and Services -> IP Host and select Add to create the local LAN.
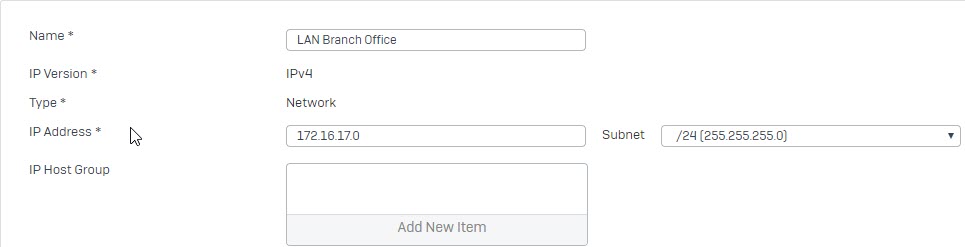
- Go to Hosts and Services -> IP Host and select Add to create the remote LAN.
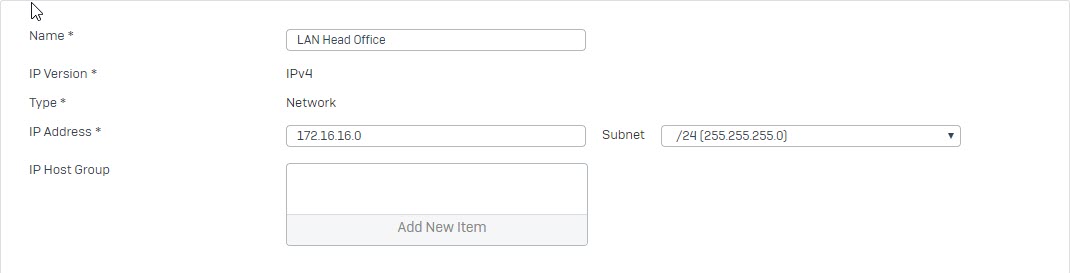
Create an IPsec VPN connection
- Go to VPN > IPsec Connections and select Wizard. Give it a name and click on Start to follow the wizard.
- Select Site To Site as a connection type and select Branch Office.
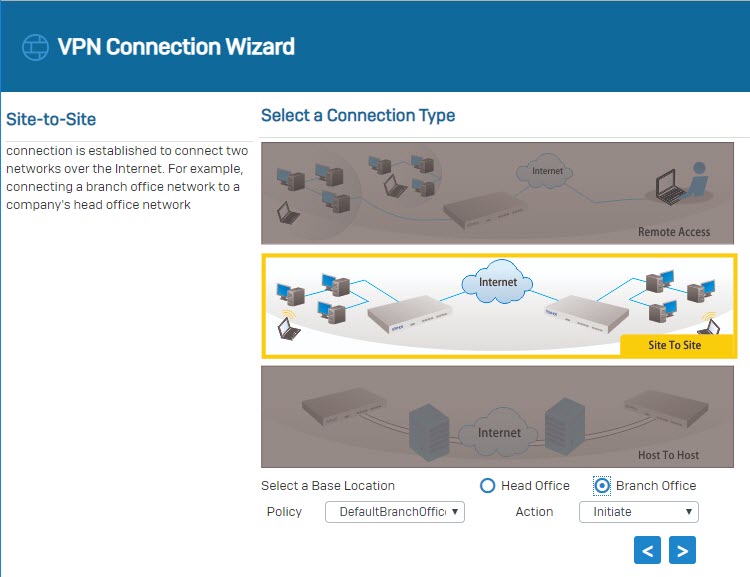
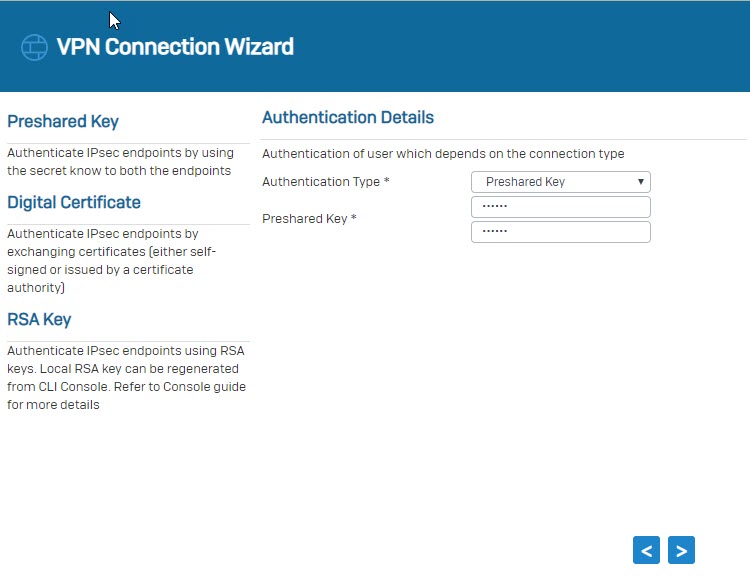
- Set the Authentication Type to preshared key.
- Make sure to use the same preshared key as in Sophos Firewall 1.
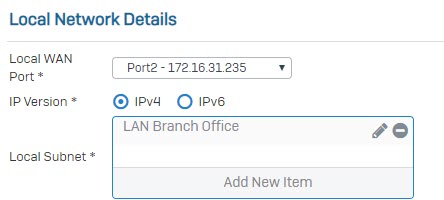
- In Local Subnet field, choose the local LAN create earlier.
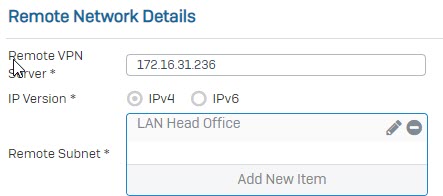
- In Remote VPN Server field, enter IP WAN of Head Office. In Remote Subnet, choose the remote LAN created earlier.
- In User Authentication Mode field, choose Disabled.
- Click Next again and click Finish.
- Click the
 under Status (Active) to activate the connection.
under Status (Active) to activate the connection.
![]()
![]()
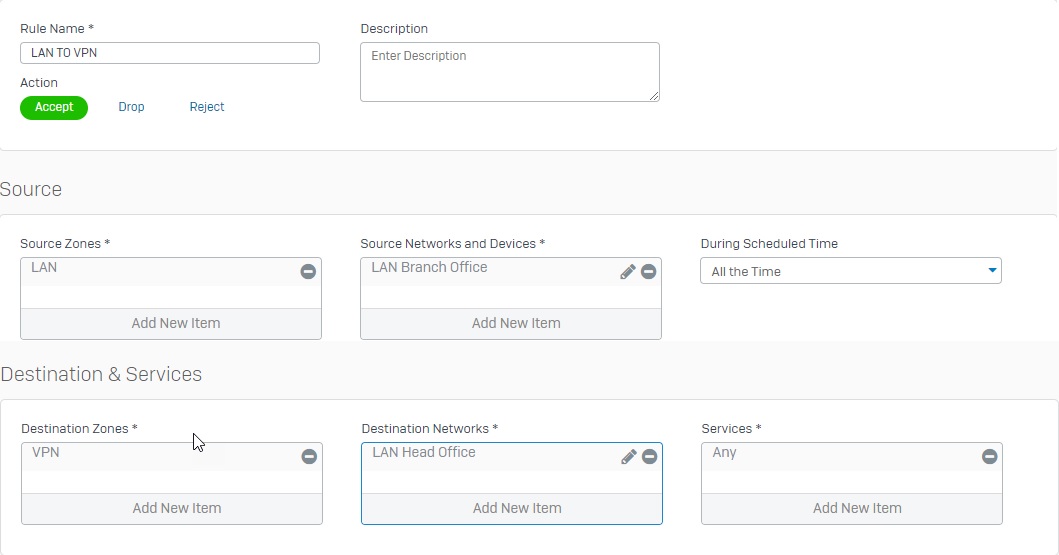
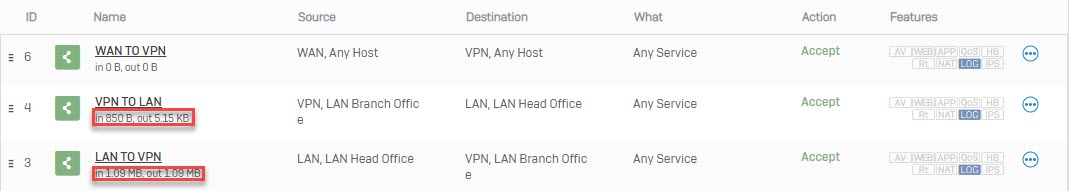
Add two firewall rules allowing VPN traffic
- Go to Firewall and click +Add Firewall Rule. Create two user/network rules as shown below.
Establishing the IPsec connection
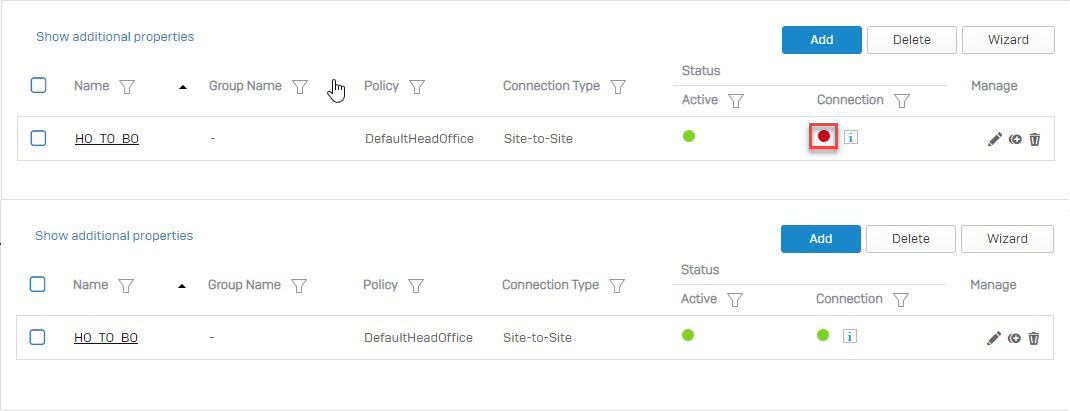
- Once both Sophos Firewall devices at the head and branch offices are configured, establish the IPsec connection between them. Go to VPN > IPsec Connections and click the
 under Status (Connection).
under Status (Connection).
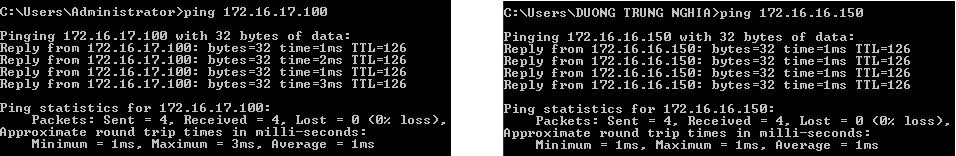
Results
- A ping test from a machine behind Sophos Firewall 1 to a machine behind Sophos Firewall 2 and vice versa should work.
- Go to Firewall and verify that VPN rules allow traffic from VPN TO LAN and LAN TO VPN.
Leave a Reply