
Overview
- Intercept X Advanced with EDR now captures all PowerShell executions so that they can be reviewed and analyzed.
- This article will guide you how to find malicious PowerShell implementations with Intercept.
Is PowerShell bad?
- Not necessarily. In fact, most PowerShell executions are not malicious, but PowerShell can be (and often is) taken advantage of.
- Intercept X already blocks known malicious PowerShell activity. The Application Lockdown feature automatically terminates a protected application based on its behavior. For example, when an Office application is leveraged to launch PowerShell, access the WMI, run a macro to install arbitrary code, or manipulate critical system areas, Sophos Intercept X will block the malicious action – even when the attack doesn’t spawn a child process. It will also prevent malicious PowerShell code executions via Dynamic Data Exchange too. Learn more about exploit protection with Intercept X.
What to do
- Login Sophos Central using your username and password.
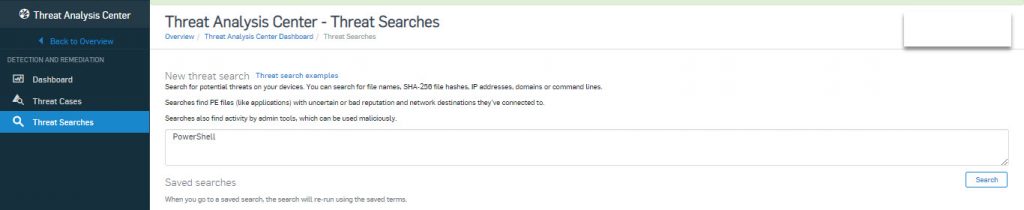
- Go to Threat Analysis Center > Threat Searcher and type PowerShell in box as shown below.
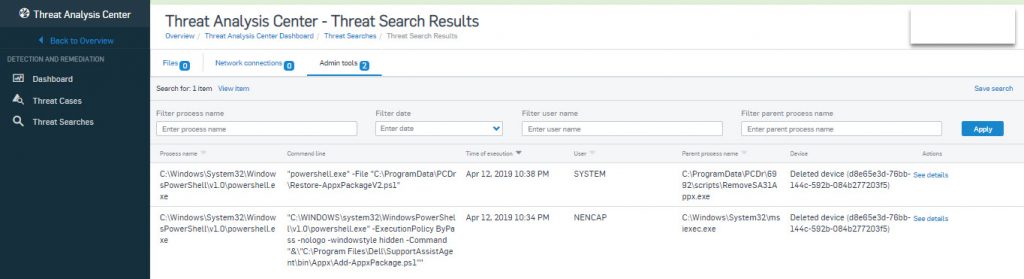
- Press Enter and select Admin Tools and we have result as shown below.
Leave a Reply