
Overview
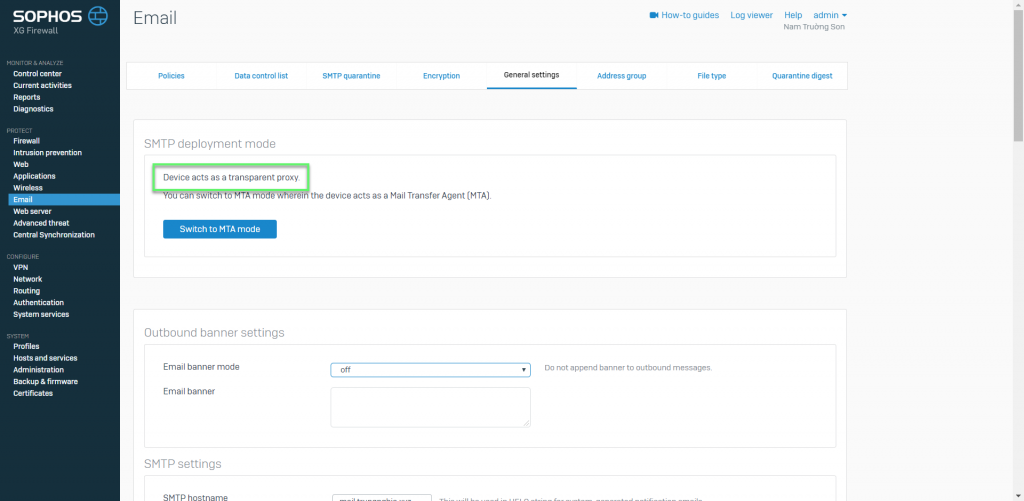
SMTP Malware Scan policies appear only when Legacy mode is enabled. The device acts as a transparent proxy
It helps protect the enterprise mail server system
How to configure
- Email -> General settings -> Check and switch to Legacy mode
- Email -> Policies
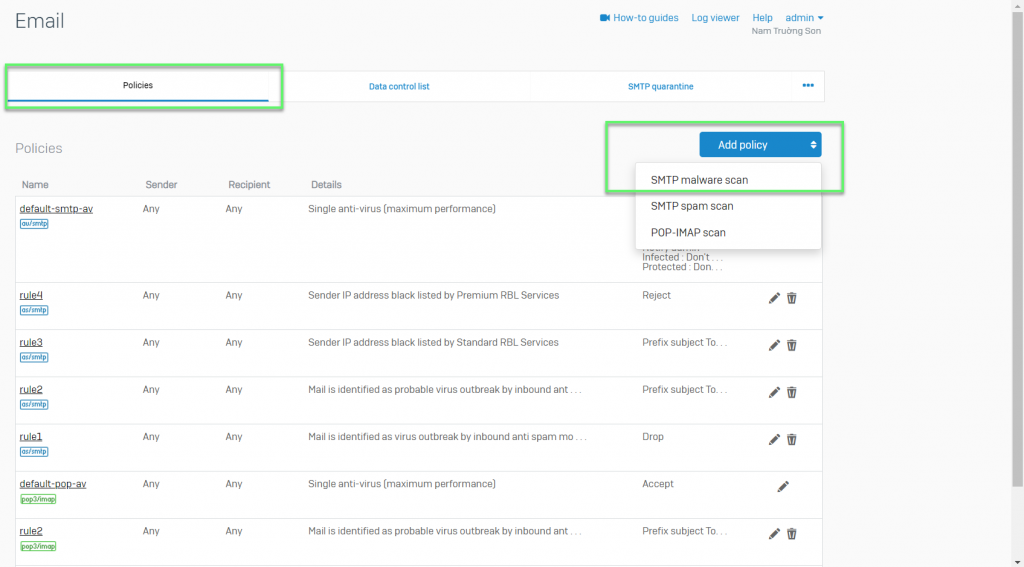
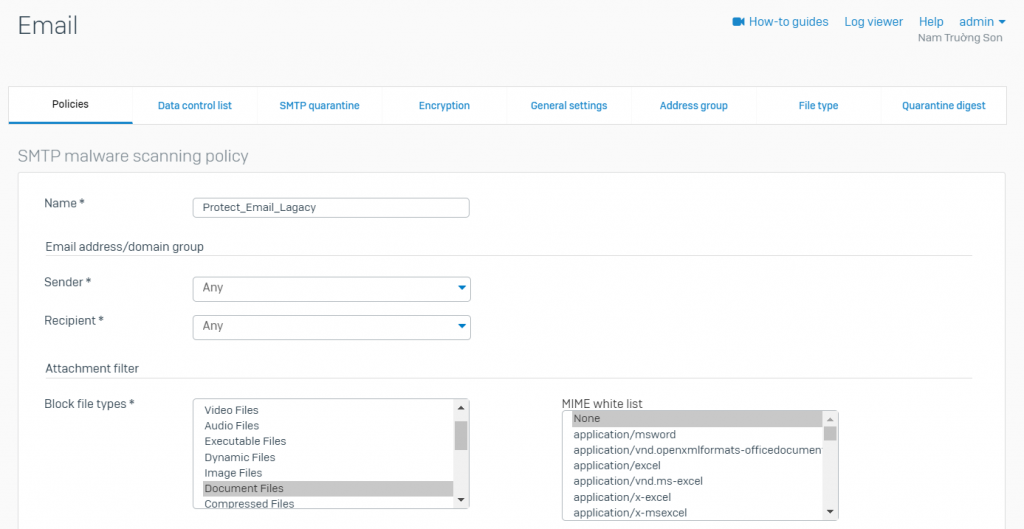
- Enter Name to identify the scan rule
- Enter Email Address/Domain Group details
- Sender: Select the sender name from the lists of users or select Any if the rule is to be applied on all the senders
- Recipient: Select the recipient name from the lists of users or select Any if the rule is to be applied on all the recipients
- Attachment Filter: Select file types to be blocked as an attachment to remove all the files that are a potential threat and to prevent virus attacks
- MIME white list: If one or more File Type is selected in Block File Type, this field is populated with the corresponding MIME Headers that belong to selected File Type. Select the MIME Header of the selected File Type. Only selected headers are to be allowed while the rest in the selected File Type are to be blocked during Anti-virus scanning of Email attachments
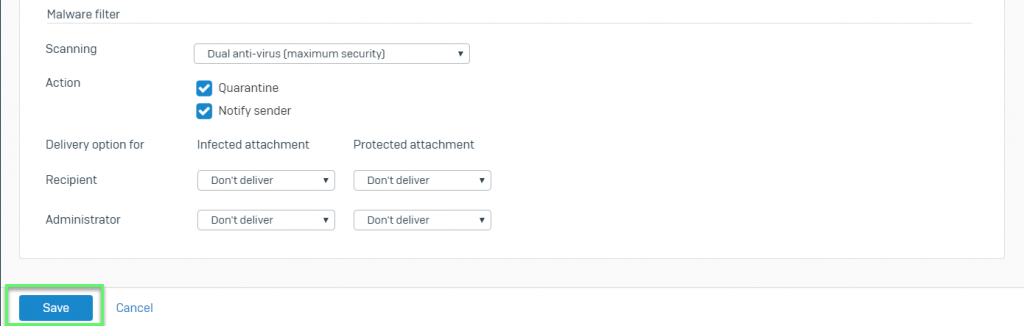
- Malware Filter: Scanning
- Disable: Emails are not scanned
- Enable: Emails are scanned by the device’s anti-virus engine
- Single Anti-virus: This primary anti-virus engine scans the emails
- Dual Anti-virus: The primary and secondary engines scan emails sequentially
- Quarantine: If enabled, copies the Email to the quarantine file list. Email is either delivered to recipient or dropped, as per configured Recipient Action.You can view the Email details like sender and receiver of the Email in the Quarantine. Administrator can access the Quarantine from Email > SMTP Quarantine while user can access from their respective User Portal
- Notify Sender: If enabled, the original message is withheld by the Device and a notification is sent to the sender informing that the Email was infected. The sender will receive the notification only if the Receiver Action is configured as Don’t Deliver
- Recipient Action
- Don’t Deliver: Receiver will not receive the message and will also not receive the notification regarding the infected Email
- Deliver Original: Receiver receives the original Email
- Remover and Deliver: Infected part of the Email is removed before delivering. Receiver will also receive the notification stating that the Email was infected and infected portion of the Email is removed. Not applicable for Blocked Attachments (Block File Type)
- Protected attachments are not scanned but receiver will be notified, if not specified otherwise
- Notify Administrator
- Don’t Deliver: Administrator will not be notified about the infected Email
- Send Original: Administrator receives the original Email
- Remove Attachment: Recipient receives message without attachment and the Administrator receives the notification that the Email attachment was infected and removed before delivering Email
- Protected attachments are not scanned but receiver will be notified, if not specified otherwise
-> Click Save
- Firewall -> Add firewall rule -> Choose Business application rule
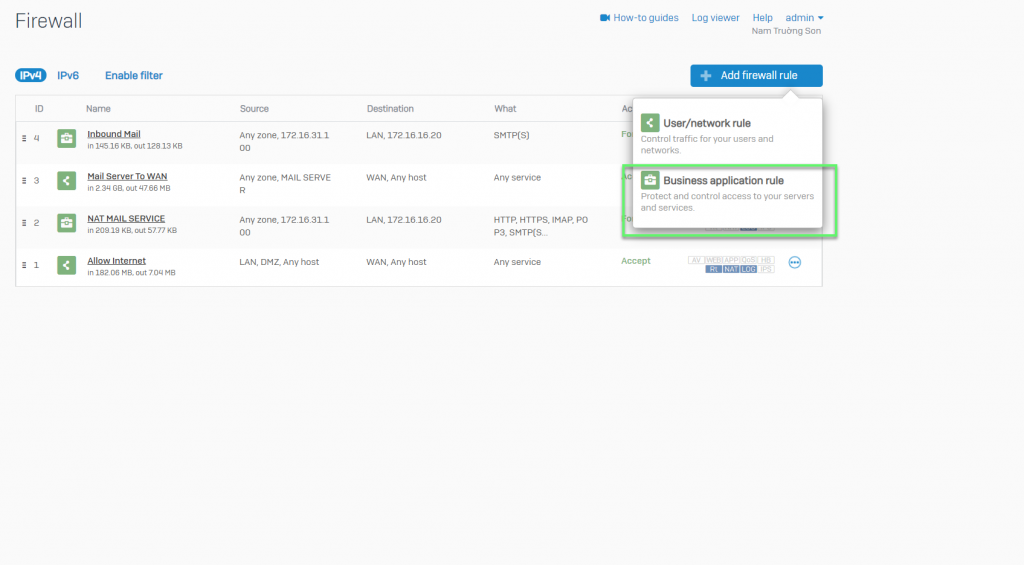
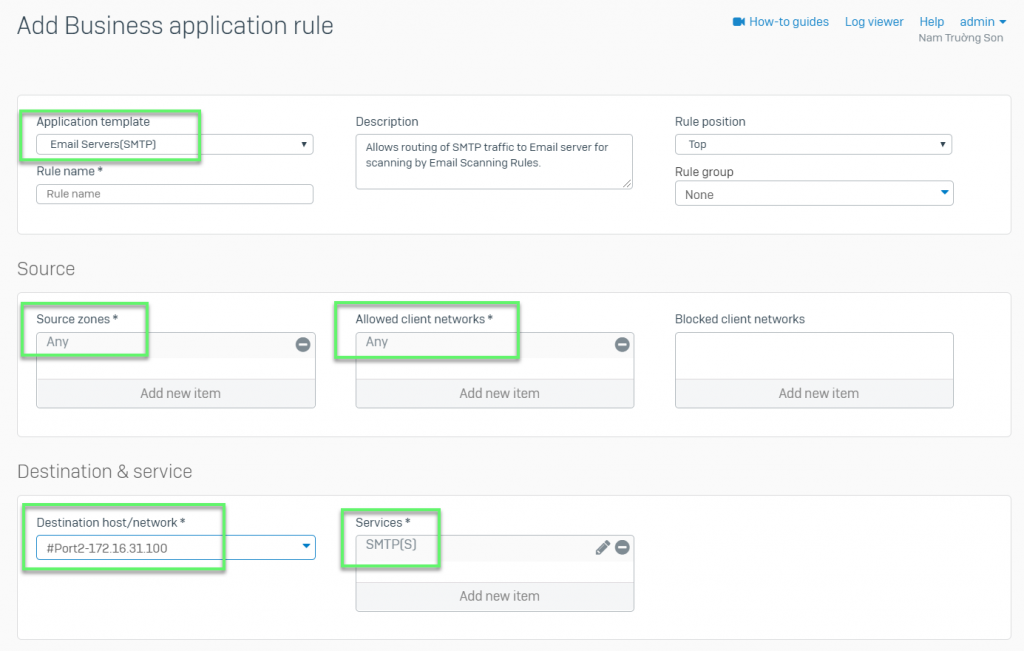
- In Application template: Choose Email Server (SMTP)
- In Source zones: Choose Any
- In Allowed client networks: Choose Any
- In Destination host/network: Choose Port WAN
- In Services: Choose SMTP(s)
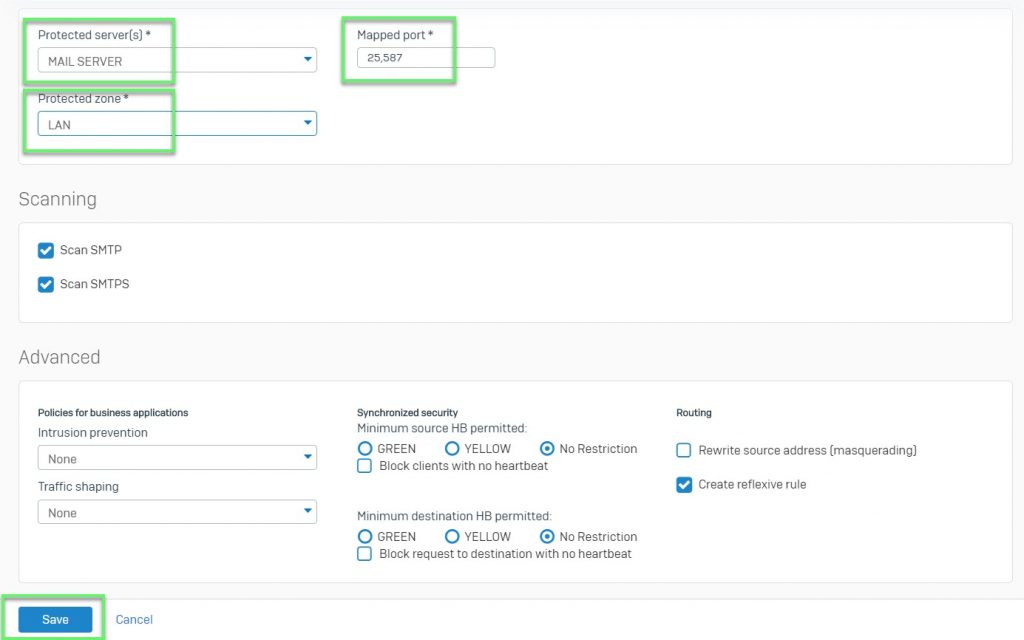
- In Protected server(s): Choose Mail server
- In Mapped port: 25,587
- In Protected zone: Choose LAN
-> Click Save
Leave a Reply