
1 Overview
Full Disk Encryption provide the capability to protect your data at highest level. It consists of protecting boot options and protecting your data, ensuring that only authenticated users can access the data.
Your data and files in your drive will be encrypted and protected, with no downtime when encrypting data.
2 Full Disk Encryption configuration
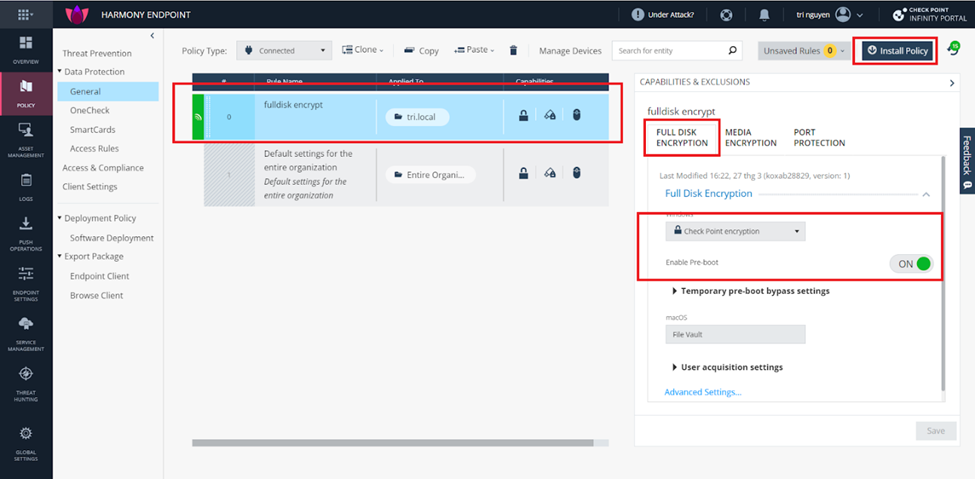
You access the policy section and create a new policy, select a group to apply your policy. Selection Checkpoint encryption type in Full disk encryption section. Turn on enable Pre-boot to protect boot. This feature protects your os of bypass tool to access illegally in your disk.
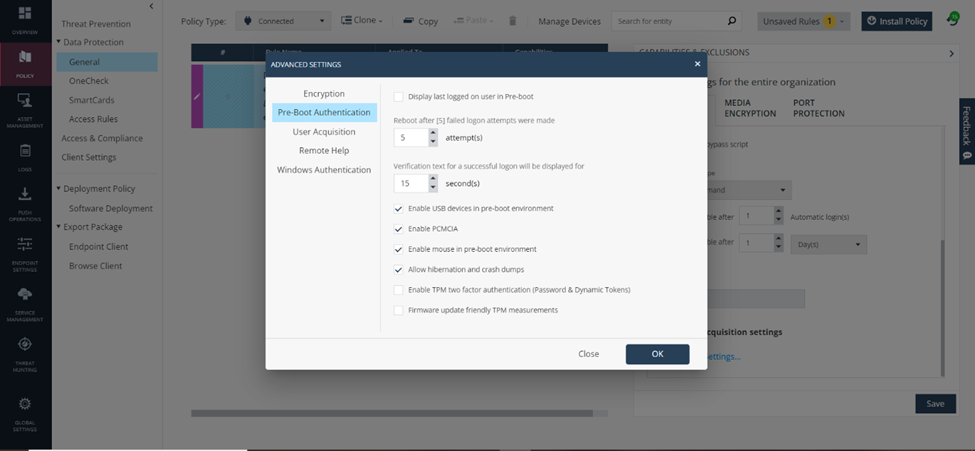
We go to advanced settings >> enable usb device, enable mouse.. to allow the use of mouse and keyboard during pre-boot. You need to enter the correct user information during the pre-boot process to be able to switch to the boot os process.
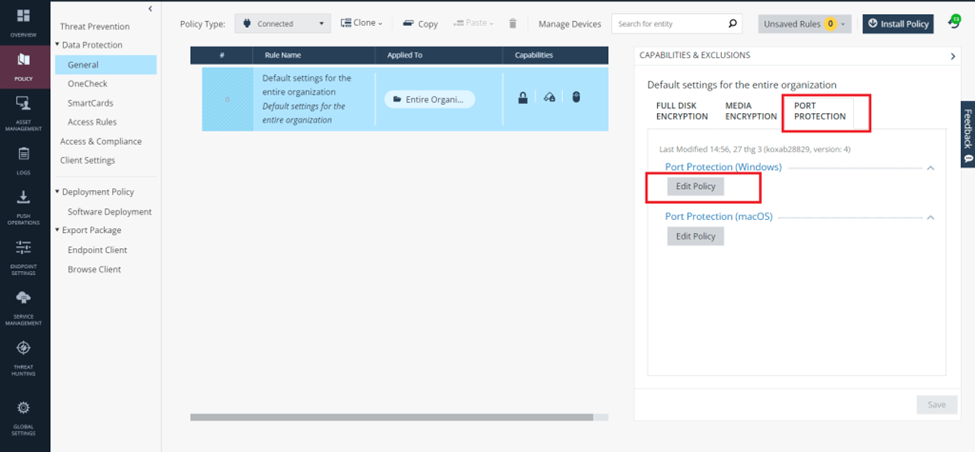
You can also go to port protection >> edit policy to allow other peripherals. This is a feature that prevents users from plugging unauthorized devices into corporate computers.
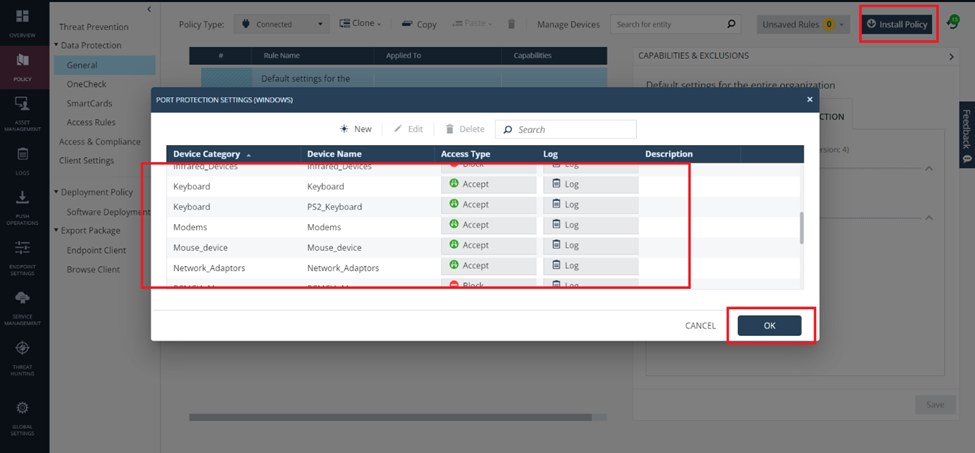
We select the device and select accept. Then press ok. We save and install the policy.
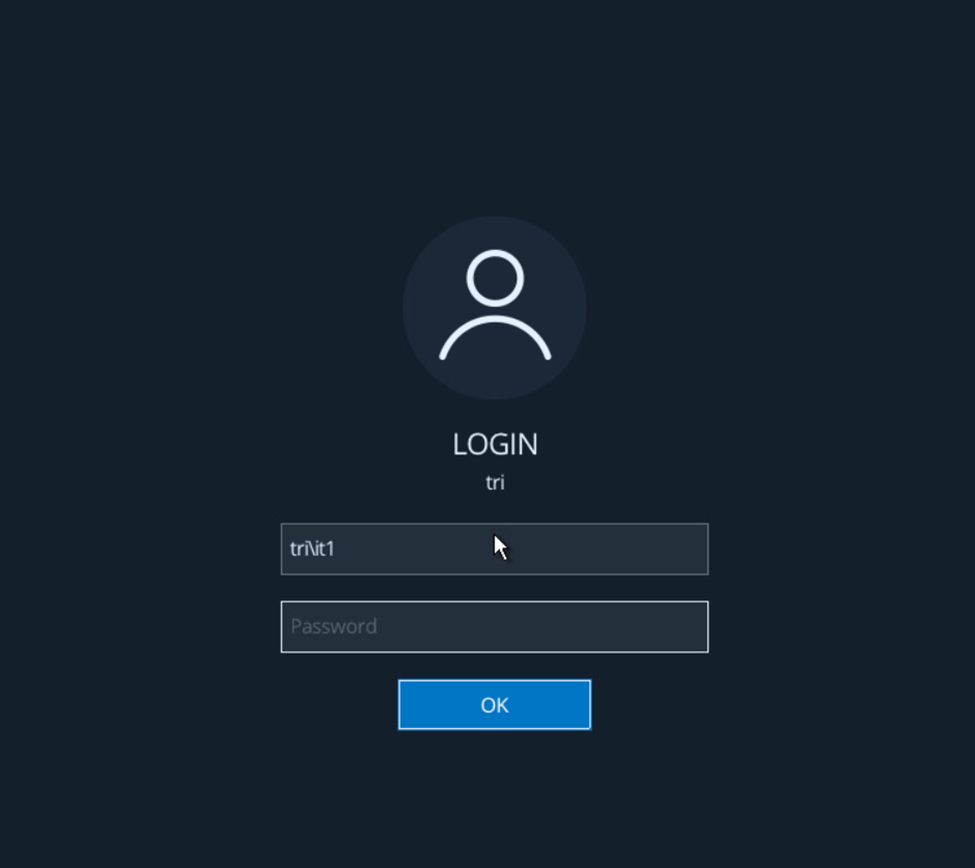
After applying the policy on the client. We update the policy and restart the client, the pre-boot login screen will appear as follows. We enter user information
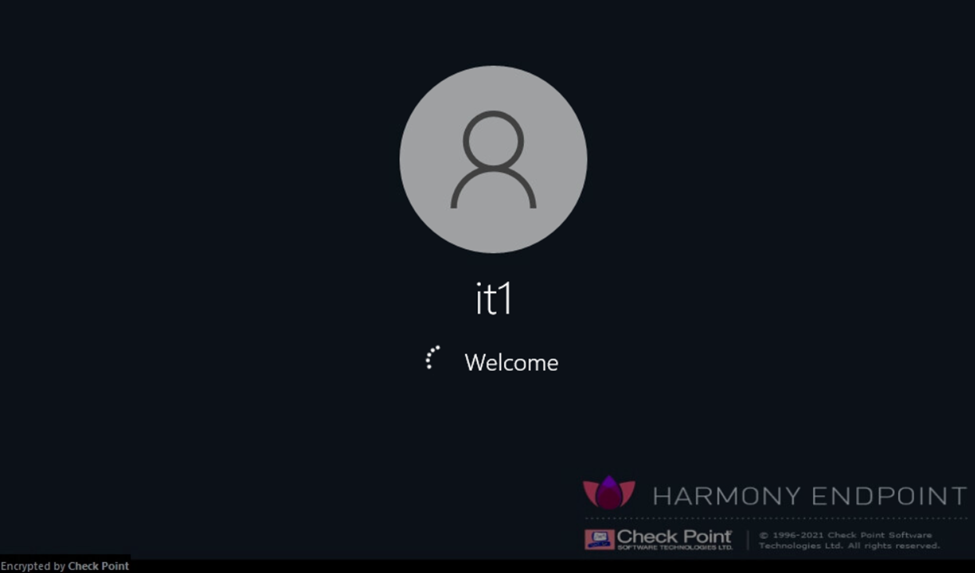
The screen shows information that this computer has been enabled Encryption. The machine will start logging into the operating system.
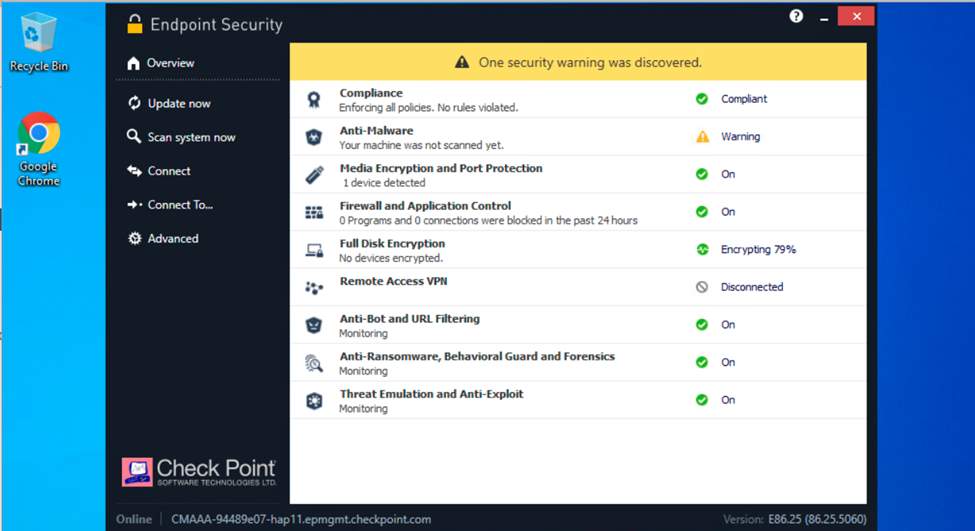
We check the overview section on the endpoint. Now the process is 79% done.
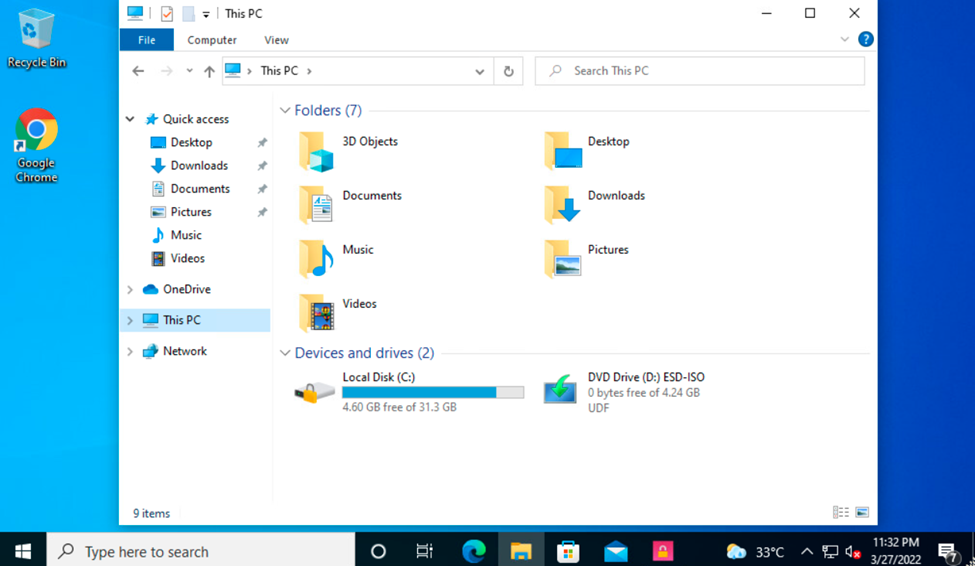
After the encryption process is completed 100%, we go to the drive section and it will show the encrypted drive as shown.
So we have successfully configured the full disk encryption feature of the harmony endpoint.
Leave a Reply