
Windows Server: How to configure WSUS function on Windows Server 2012
Overview Microsoft Windows Server Update Services (WSUS) is an effective solution for businesses in system update issues. WSUS offers a solution to this problem, WSUS Read More

Overview Microsoft Windows Server Update Services (WSUS) is an effective solution for businesses in system update issues. WSUS offers a solution to this problem, WSUS Read More

Overview Microsoft is trying to solve a problem that has long existed for Windows users, that is how to run an unknown .exe file on Read More
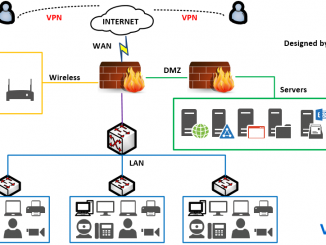
Overview This article describes a network with 2 firewall devices that helping protect LAN network and DMZ network Drawing Description The network diagram helps the Read More

Overview How to configure Step 1: Download Agent Source Code Download the Agent installation package according to the respective operating system, in this case Windows: Read More

Overview Intercept X Advanced with EDR now captures all PowerShell executions so that they can be reviewed and analyzed. This article will guide you how Read More

Overview This article provides information on how to reset the admin password on the Sophos XG Firewall. Configuring Via SFLoader Connect the console cable and Read More

Overview Zabbix is an open source enterprise software that monitors networks and applications It is designed to help network administrators monitor and monitor the status Read More

Overview Nowdays, everyone use MS Outlook as mail tool to Send/Receive the email for my daily work. I ensure that you did not want to Read More

Overview Cryptocurrency is a digital or virtual coin that uses encryption for security. Because they are anonymous and decentralized, many people can use them for Read More

Create proceses Lists the jobs running in the background, giving the job number Bring a background job to the foreground Change suspend the current foreground Read More
Copyright © 2025 | WordPress Theme by MH Themes